September 11 2025
真香!IPFLY+ixBrowser指纹浏览器,超高性价比跨境工具组合来了!
在当今全球化的商业环境中,跨境电商已成为众多企业拓展市场的重要途径。而在跨境电商领域,指纹浏览器和独立纯享代理IP的结合,无疑为商家们提供了强大的助力。
指纹浏览器作为一种创新的工具,具有诸多优势。它可以修改浏览器指纹信息,有效避免账号关联问题。
而优质纯享的IP更是跨境电商中不可或缺的一部分。通过连接到其他国家或地区的服务器,代理IP可以帮助用户绕过地理限制和访问限制,提供更高的网络匿名性和安全性。
尤其是现在大火的TikTok,很多人苦恼的多账号管理、批量养号、批量视频发布都可以通过使用

ixBrowser指纹浏览器是什么?
ixBrowser 是一款永久免费的指纹浏览器。
借助其优秀的指纹隔离技术,你的指纹环境在第三方检测网站Pixelscan和Iphey的检测下拥有非常高的通过率,不论是跨境电商人士,还是在线营销人员都可以轻松管理多个独立账号,同时规避平台检测封禁。
同时,用户可以免费无限制创建独立窗口并邀请团队成员,极大节省运营成本及运营时间。
以IPFLY静态原生IP为例,如何在ixBrowser配置IP?
1、首先,你需要先购买IPFLY静态原生IP,进入
(注:ixBrowser用户现在购买套餐可享受专属8折优惠,折扣码【IP6688】)
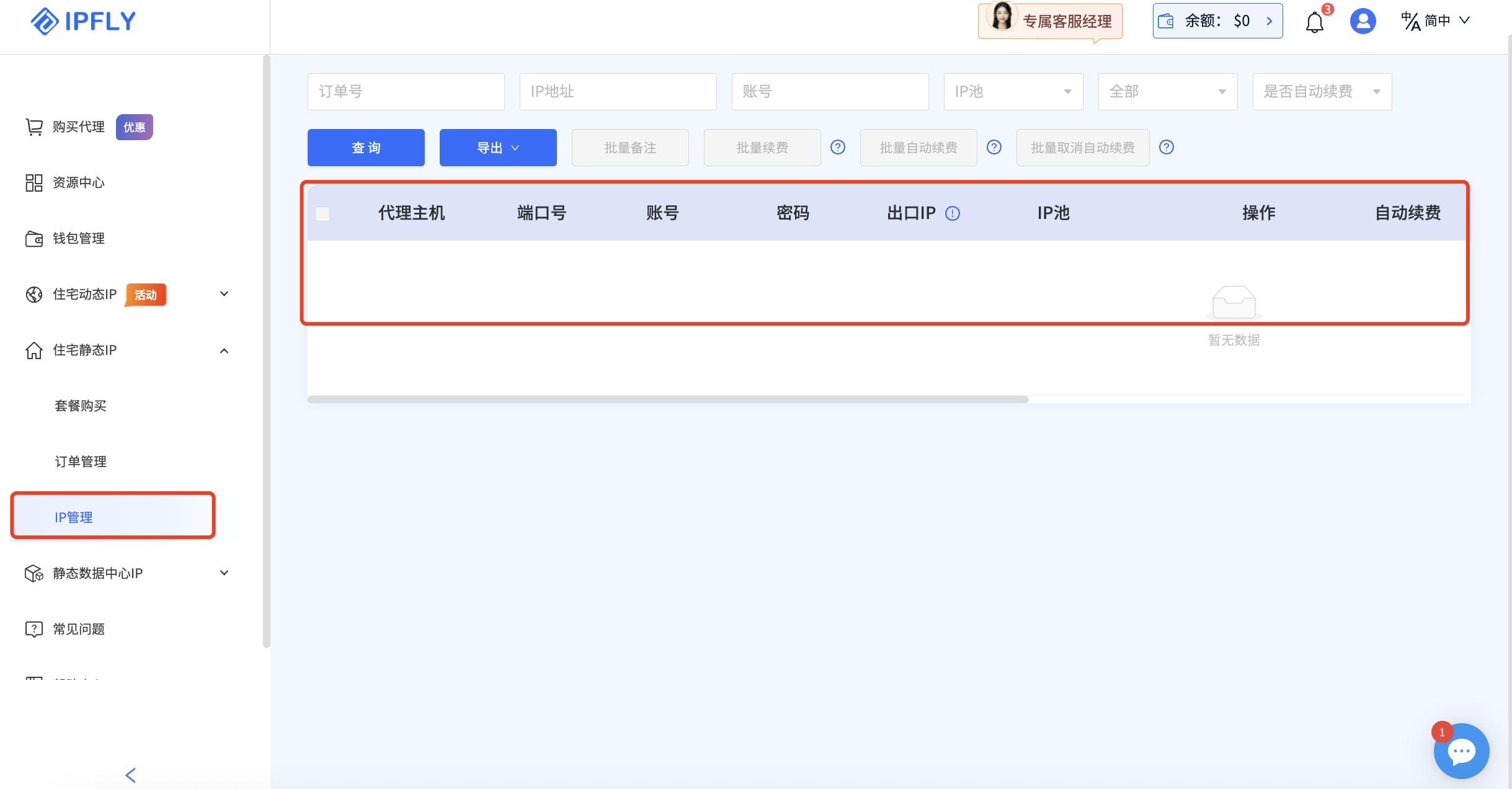
2、支付成功之后,就可以在住宅静态IP-IP管理里面找到我们刚刚买好的IP;
3、下载并注册
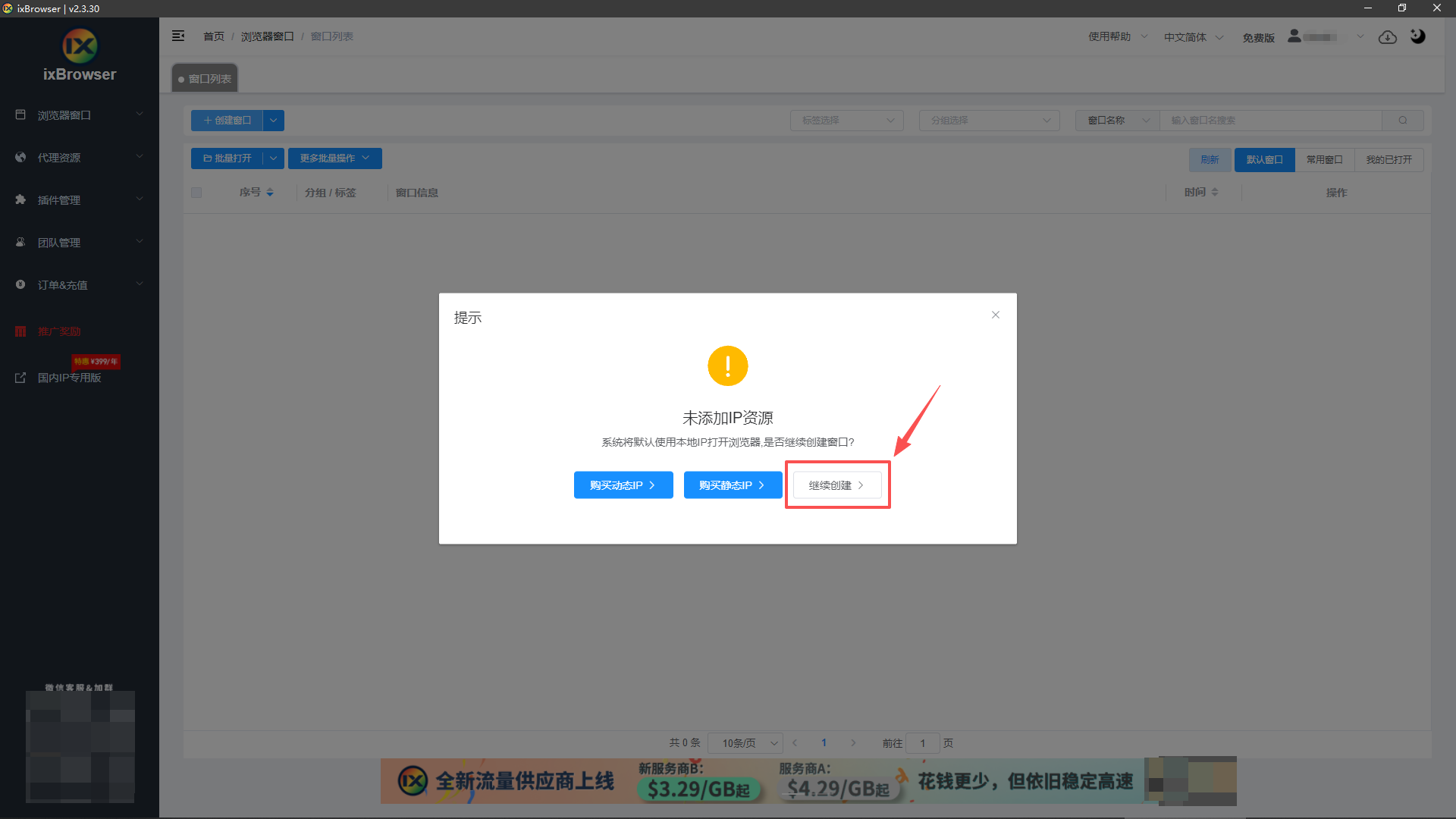
4、出现提示后,选择继续创建;
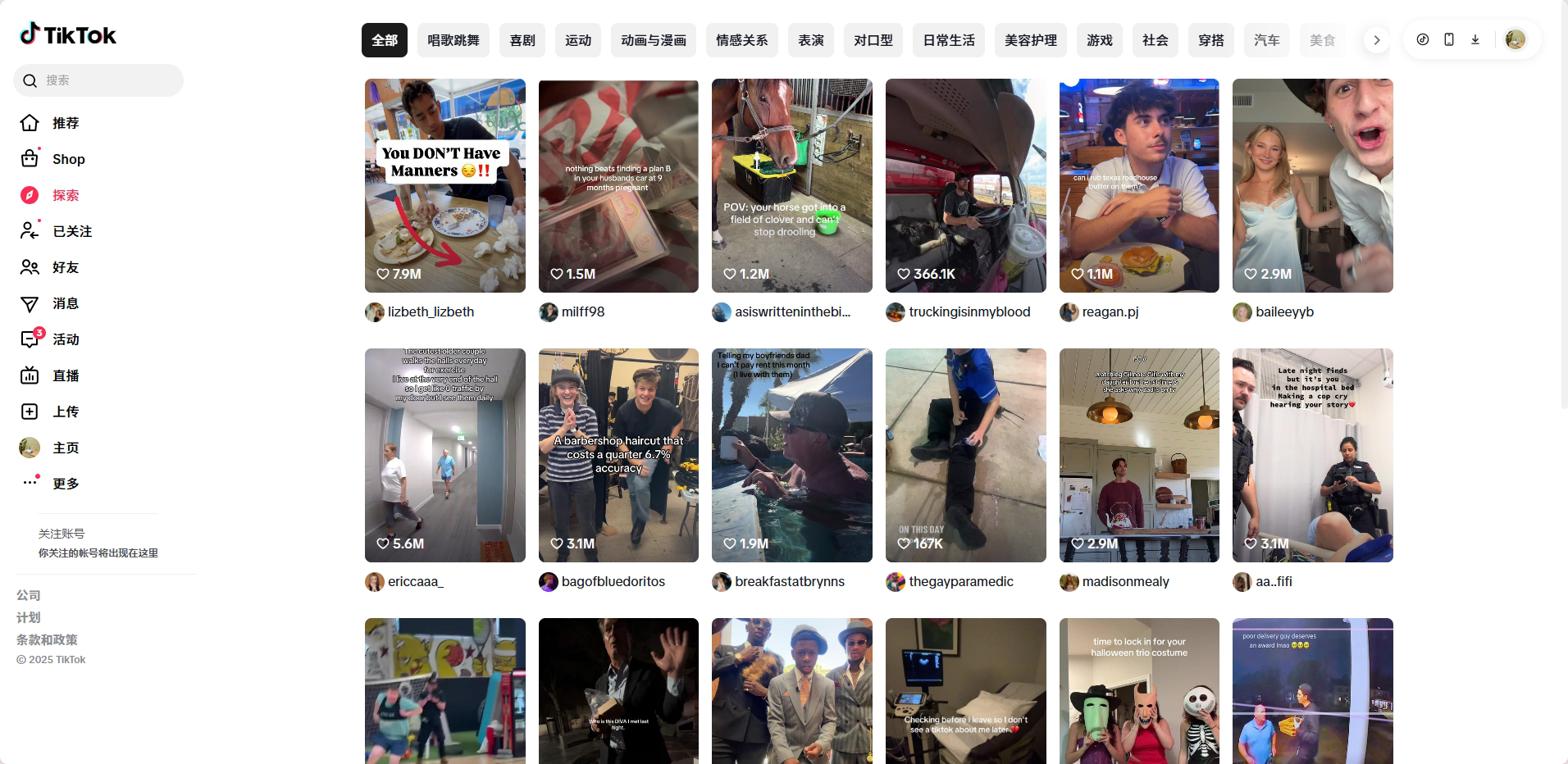
5、根据自己的实际情况填写平台账号配置,如下图,我们需要管理的是TikTok账号,把自己的账号信息填入即可;
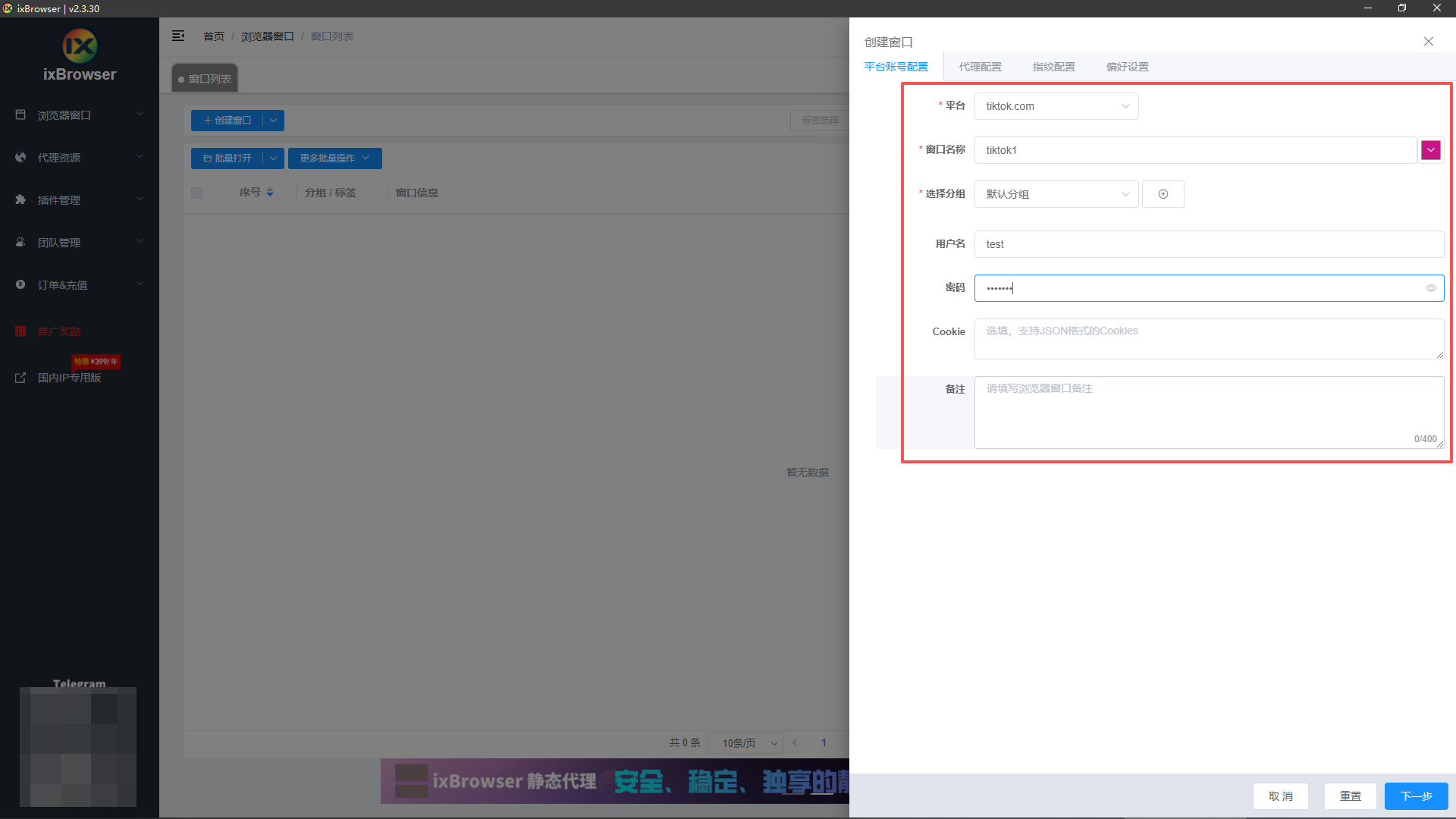
6、点击代理配置,将我们在IPFLY购买的静态原生IP信息填入;
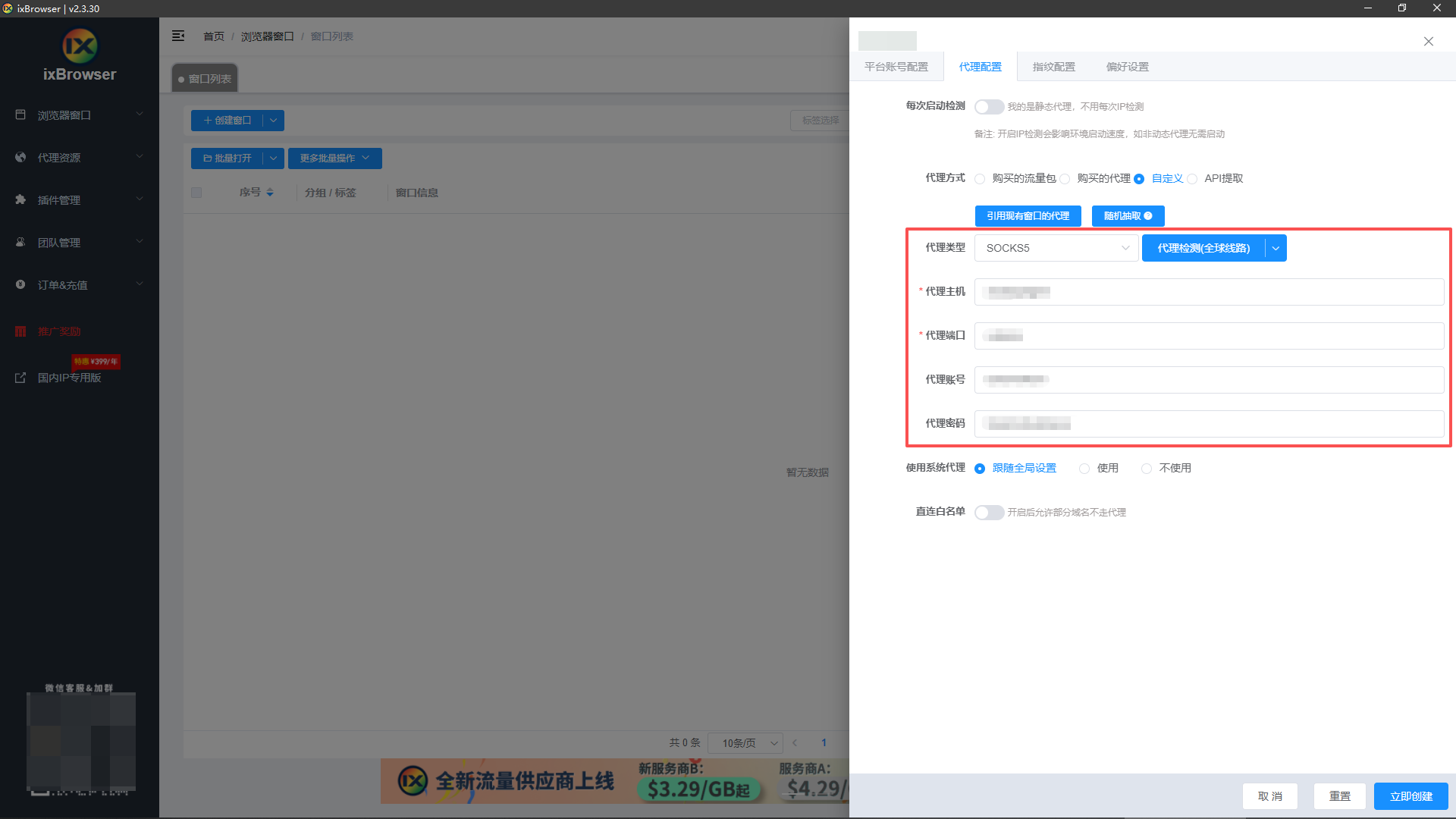
7、再将指纹设置和偏好设置按照需求填写好,最后点击立即创建即可;
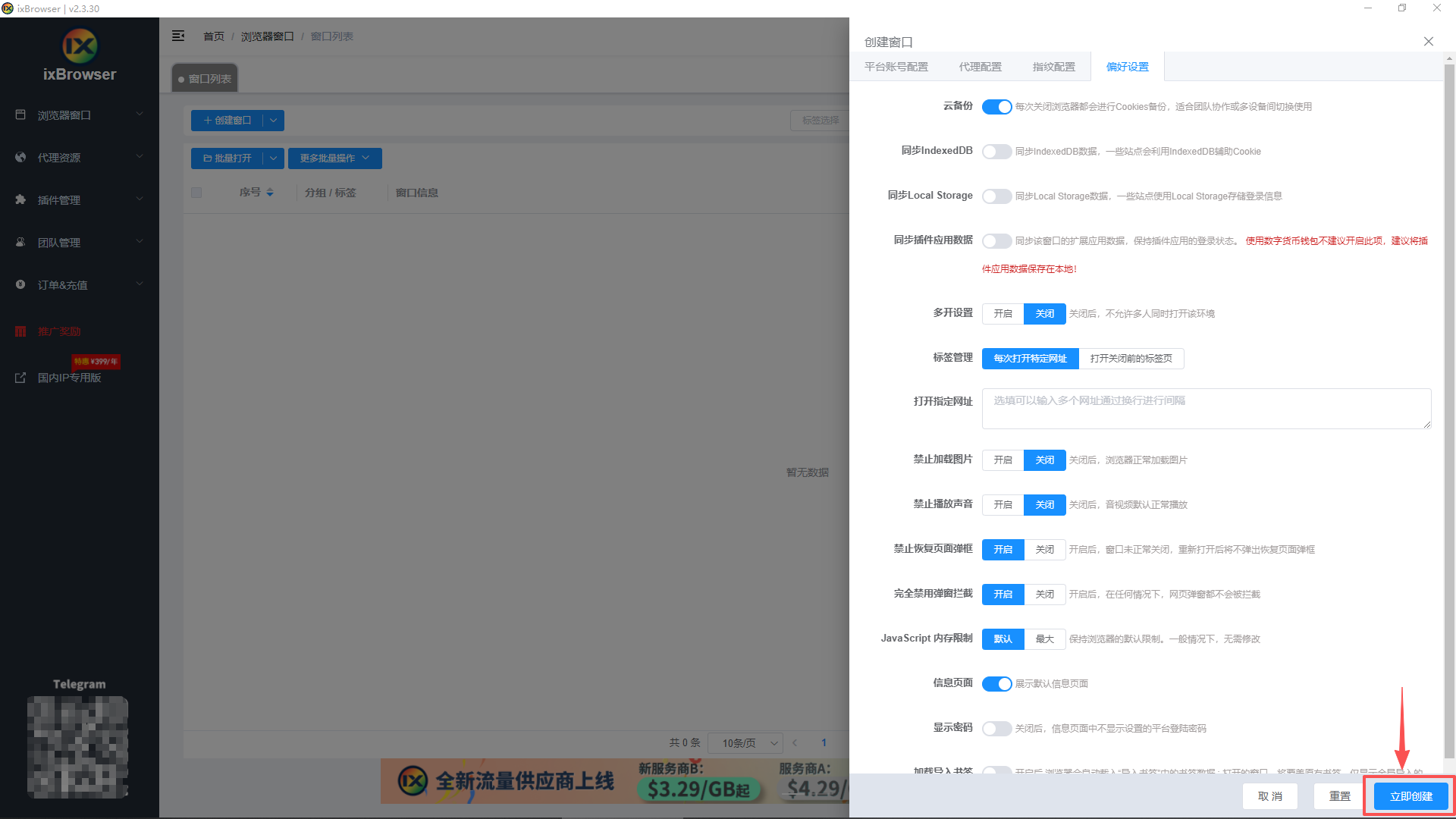
8、然后页面就会显示我们配置成功的环境;
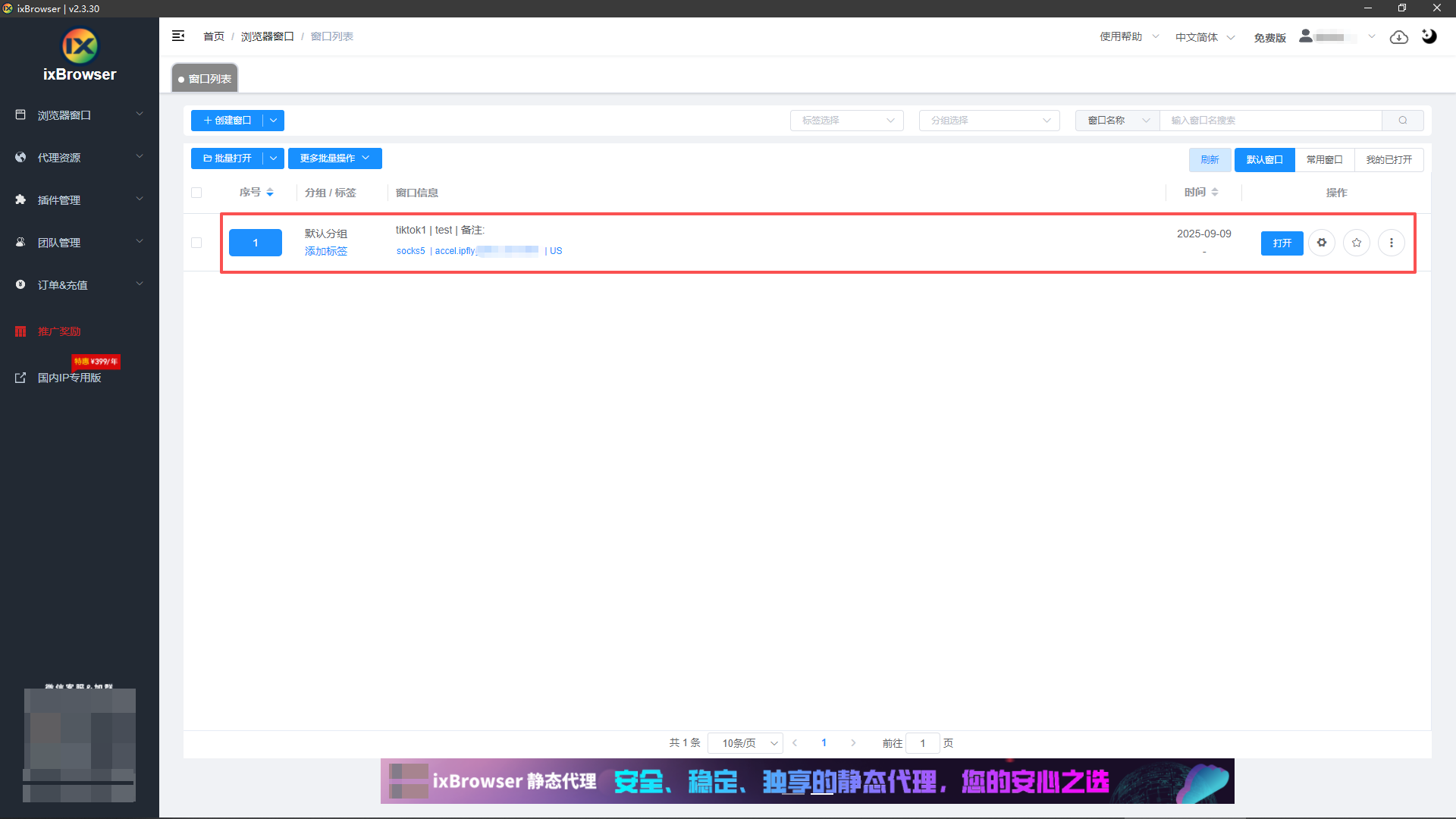
9、点击打开,你就会进入一个独立的TikTok账号页面,然后就可以进行一系列的养号、发布视频等操作
注:以上需要用户在海外网络环境下操作
如果有多个TikTok账号,购买完IP后按以上步骤重复操作或者在ixBrowser指纹浏览器批量导入就可以。
当然,ixBrowser指纹浏览器和IPFLY代理IP的结合,肯定不局限于在社媒平台TikTok业务侧提供强大的支持。
ixBrowser指纹浏览器支持海外所有的网站平台,IPFLY更是可以通过不同的业务场景提供更适合你的IP类型,以此帮助商家们在全球市场中脱颖而出,实现商业增长。
一键注册/下载通道
IPFLY:
ixBrowser:
指纹浏览器作为一种创新的工具,具有诸多优势。它可以修改浏览器指纹信息,有效避免账号关联问题。
而优质纯享的IP更是跨境电商中不可或缺的一部分。通过连接到其他国家或地区的服务器,代理IP可以帮助用户绕过地理限制和访问限制,提供更高的网络匿名性和安全性。
尤其是现在大火的TikTok,很多人苦恼的多账号管理、批量养号、批量视频发布都可以通过使用
IPFLY的静态原生IP
搭配免费指纹浏览器ixBrowser
实现高效又稳定的运营效果。
ixBrowser指纹浏览器是什么?

ixBrowser 是一款永久免费的指纹浏览器。
借助其优秀的指纹隔离技术,你的指纹环境在第三方检测网站Pixelscan和Iphey的检测下拥有非常高的通过率,不论是跨境电商人士,还是在线营销人员都可以轻松管理多个独立账号,同时规避平台检测封禁。
同时,用户可以免费无限制创建独立窗口并邀请团队成员,极大节省运营成本及运营时间。
以IPFLY静态原生IP为例,如何在ixBrowser配置IP?
1、首先,你需要先购买IPFLY静态原生IP,进入
IPFLY官网
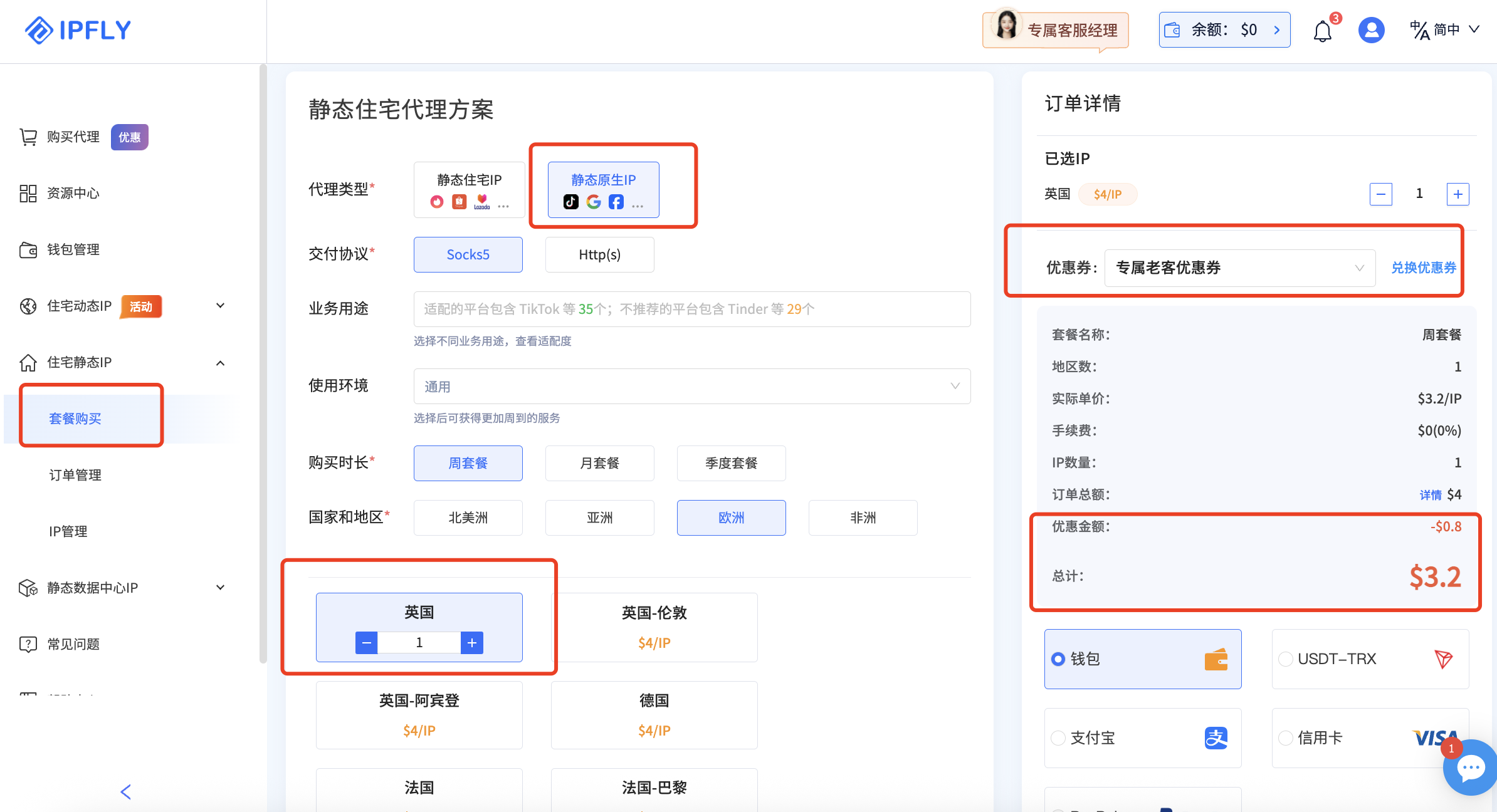
,注册账号后登录后台,点击住宅静态IP-套餐购买-静态原生IP,找到你想要的国家购买即可;

(注:ixBrowser用户现在购买套餐可享受专属8折优惠,折扣码【IP6688】)
2、支付成功之后,就可以在住宅静态IP-IP管理里面找到我们刚刚买好的IP;

3、下载并注册
ixBrowser指纹浏览器
,登录后台并点击创建窗口;

4、出现提示后,选择继续创建;

5、根据自己的实际情况填写平台账号配置,如下图,我们需要管理的是TikTok账号,把自己的账号信息填入即可;

6、点击代理配置,将我们在IPFLY购买的静态原生IP信息填入;

7、再将指纹设置和偏好设置按照需求填写好,最后点击立即创建即可;

8、然后页面就会显示我们配置成功的环境;

9、点击打开,你就会进入一个独立的TikTok账号页面,然后就可以进行一系列的养号、发布视频等操作

注:以上需要用户在海外网络环境下操作
如果有多个TikTok账号,购买完IP后按以上步骤重复操作或者在ixBrowser指纹浏览器批量导入就可以。
当然,ixBrowser指纹浏览器和IPFLY代理IP的结合,肯定不局限于在社媒平台TikTok业务侧提供强大的支持。
ixBrowser指纹浏览器支持海外所有的网站平台,IPFLY更是可以通过不同的业务场景提供更适合你的IP类型,以此帮助商家们在全球市场中脱颖而出,实现商业增长。
一键注册/下载通道
IPFLY:
https://console.ipfly.net/register
ixBrowser:
https://www.ixbrowser.com/code/FJI3

September 02 2025
BestProxy: The world's leading high-quality proxy server
When conducting market research or advertising campaigns, it is often necessary to use multiple IP addresses in order to avoid identification and subsequent banning by platforms. This is particularly important when collecting large amounts of data from different regions, as frequent IP address changes are essential. However, traditional proxy services often have unstable connections or limited coverage, which can affect efficiency.

Introduction
· Massive IP coverage: Provides access to over 80 million residential IP addresses in more than 200 countries and regions for global data scraping.
· Multiple proxy types: Residential proxies, unlimited residential proxies, static residential proxies, static data centre proxies, long-term ISP proxies and web scraper APIs are included to meet various business needs.
· High anonymity and stability: IP availability exceeds 99%, ensuring high network connection stability and anonymity.
· Flexible usage modes: Supports IP randomisation and sticky IP modes, offering pay-per-traffic or unlimited traffic plans to accommodate diverse data collection requirements.
· Easy integration and management: IPs can be managed via user authentication/API, and the data collection process is simplified by the provision of rich crawler templates and code examples.
· Free trial and comprehensive support: The Web Scraper API offers a free trial for 30 days, helping to reduce development and maintenance costs.
Locations
BestProxy offers residential proxies from over 200 countries, covering major regions around the world, including North America, South America, Europe, Asia, Oceania, Antarctica, and Africa, ensuring that you can quickly and stably access data from all over the world.
Proxy types
1.
2.
3.
4.
5.
6.
BestProxy provides flexible, efficient and stable services for each proxy type to ensure they meet a range of business needs.
Application cases
1. Market research: Accurately obtain data from around the world to expand large-scale businesses and conduct market research.
2. Advertising verification: Check how advertisements are displayed in different regions to ensure they are effective.
3. Social media management: Manage social media accounts, avoid bans and promote business growth.
4. E-commerce: Help cross-border e-commerce companies to monitor their competitors' prices and information in order to optimise their pricing strategies.
5. Web scraping: Extract real-time data from global websites to support automated data extraction and save development time.
Service features
· Easy integration: Provides a simple API for straightforward connection with various tools and software, simplifying user operations.
· Comprehensive support: 24/7 customer support ensures users can get help and resolve issues at any time.
· Scalability: Supports on-demand expansion to meet the needs of a growing business and is suitable for various industry applications.
Come and try
BestProxy
's global proxy server service was created to address these issues.
Introduction
BestProxy
offers premium proxy services trusted worldwide. With over 80 million residential IP addresses covering more than 200 countries and regions, BestProxy ensures high stability and fast connections. Our service provides easy integration through a simple API and supports both HTTP and SOCKS5 protocols. With scalable solutions for growing businesses, BestProxy is widely used in advertising, testing, market research, and social media management.· Massive IP coverage: Provides access to over 80 million residential IP addresses in more than 200 countries and regions for global data scraping.
· Multiple proxy types: Residential proxies, unlimited residential proxies, static residential proxies, static data centre proxies, long-term ISP proxies and web scraper APIs are included to meet various business needs.
· High anonymity and stability: IP availability exceeds 99%, ensuring high network connection stability and anonymity.
· Flexible usage modes: Supports IP randomisation and sticky IP modes, offering pay-per-traffic or unlimited traffic plans to accommodate diverse data collection requirements.
· Easy integration and management: IPs can be managed via user authentication/API, and the data collection process is simplified by the provision of rich crawler templates and code examples.
· Free trial and comprehensive support: The Web Scraper API offers a free trial for 30 days, helping to reduce development and maintenance costs.
Locations
BestProxy offers residential proxies from over 200 countries, covering major regions around the world, including North America, South America, Europe, Asia, Oceania, Antarctica, and Africa, ensuring that you can quickly and stably access data from all over the world.

Proxy types
1.
Residential Proxies
: These provide real residential IP addresses, ensuring high anonymity and privacy protection while avoiding blocking and supporting IP randomisation and sticky IP mode.2.
Unlimited Residential Proxies
: Offer 100+ Gbps bandwidth, making it suitable for large-scale data collection and LLM training. Support unlimited concurrent requests.3.
Static Residential Proxies
: There are no traffic restrictions and it offers 99.9% uptime, making it suitable for enterprise data scraping and market research.4.
Static Data Centre Proxies
: It provides the fastest 100% anonymous IPs to ensure efficient data collection and global coverage.5.
Long Acting ISP Proxies
: Billed by traffic. Supports unlimited connections and threads. Suitable for scenarios requiring long-term, stable proxies.6.
Web Scraper APIs
: A 30-day free trial is offered with no need for development or self-hosted servers. Real-time data scraping from hundreds of global websites simplifies development and maintenance.BestProxy provides flexible, efficient and stable services for each proxy type to ensure they meet a range of business needs.
Application cases
1. Market research: Accurately obtain data from around the world to expand large-scale businesses and conduct market research.
2. Advertising verification: Check how advertisements are displayed in different regions to ensure they are effective.
3. Social media management: Manage social media accounts, avoid bans and promote business growth.
4. E-commerce: Help cross-border e-commerce companies to monitor their competitors' prices and information in order to optimise their pricing strategies.
5. Web scraping: Extract real-time data from global websites to support automated data extraction and save development time.
Service features
· Easy integration: Provides a simple API for straightforward connection with various tools and software, simplifying user operations.
· Comprehensive support: 24/7 customer support ensures users can get help and resolve issues at any time.
· Scalability: Supports on-demand expansion to meet the needs of a growing business and is suitable for various industry applications.
Come and try
BestProxy
, gain access to global data, protect your network privacy and stay at the forefront of technology! Click the service link in the bottom right-hand corner for 10% off and 24/7 support.
August 20 2025
批量养号更安心!用 ixBrowser 高效搞定 TikTok 电脑端批量养号
在跨境电商、内容创作和营销领域,TikTok 矩阵账号运营已成为流量变现的核心策略,而 “养号” 作为账号运营的基石,尤其是批量养号,需要既安全又高效的方法。本文将聚焦如何借助 ixBrowser,在电脑端实现 TikTok 批量养号的全流程操作,助你避开风控雷区,让多账号运营更稳定。
简单来说,养号是指账号注册初期或长期未活跃后,通过模拟真实用户的刷视频、点赞、关注等行为,逐步提升账号权重和信誉度的过程。
TikTok 算法会通过分析账号的活跃度、行为规律、互动质量等维度,判断账号是否为 “真实可靠的用户”。养号的核心目标就是让算法认定你的账号是 “真人活跃账号”,从而获得更多推荐流量,降低限流、封号风险。例如,一个每天自然刷视频 20 分钟、适度点赞评论的账号,更容易被系统判定为 “优质用户” 并给予曝光;而刚注册就狂发广告或批量操作的账号,则可能触发风控。
以下流程从注册到内容发布,循序渐进帮助账号积累权重,全程可结合 ixBrowser 优化操作:
批量养号的难点在于 “多账号独立化”,而 ixBrowser 通过以下功能精准破解:
1.账号关联风险(共享设备 / IP)
生成独立设备指纹(包括浏览器版本、字体、时区等),每个账号绑定专属代理 IP,实现设备与网络环境完全隔离;
2.网络环境频繁变更引发账号异常
什么是 TikTok 养号?
简单来说,养号是指账号注册初期或长期未活跃后,通过模拟真实用户的刷视频、点赞、关注等行为,逐步提升账号权重和信誉度的过程。TikTok 算法会通过分析账号的活跃度、行为规律、互动质量等维度,判断账号是否为 “真实可靠的用户”。养号的核心目标就是让算法认定你的账号是 “真人活跃账号”,从而获得更多推荐流量,降低限流、封号风险。例如,一个每天自然刷视频 20 分钟、适度点赞评论的账号,更容易被系统判定为 “优质用户” 并给予曝光;而刚注册就狂发广告或批量操作的账号,则可能触发风控。
为什么选择电脑端批量养号?
尽管 TikTok 以移动端为主,但批量养号阶段,电脑端操作优势显著:- 多账号管理更高效:电脑可同时打开多个窗口,相比手机频繁切换账号的繁琐,电脑端能快速切换、并行操作,尤其适合矩阵团队协作。
- 自动化工具适配性更强:电脑端可搭配各类自动化脚本工具,实现刷视频、互动等行为的自动执行,效率远超移动端(受系统权限限制,移动端自动化工具稳定性较差)。
- 网络环境更稳定:电脑多连接有线或固定 Wi-Fi,网络波动小,减少因网络异常导致的账号登录风险;而手机网络不稳定时,易触发安全验证或风控。
- 数据监控更便捷:电脑屏幕更大,可同时查看多个账号的状态数据,搭配分析工具能快速调整养号策略。
TikTok 养号全流程(附 ixBrowser 适配技巧)
以下流程从注册到内容发布,循序渐进帮助账号积累权重,全程可结合 ixBrowser 优化操作:
第一阶段:账号注册与基础设置(第 1 天)
- 搭建稳定网络环境
注册时需保证 IP 地址固定,避免频繁更换地区或网络。借助 ixBrowser 的 “代理配置” 功能,可为每个账号分配专属 IP,确保 IP 与目标市场匹配,从源头降低异常登录风险。 - 完善账号基础信息
- 上传清晰、非广告化的头像;
- 昵称和简介需贴近普通用户风格,避免营销感;
- 选择与账号定位相关的标签,帮助系统初步识别兴趣。
- 避免立即发布内容
新账号首日不建议发视频,先通过 ixBrowser 打开 TikTok 网页版,模拟真实用户浏览行为,让账号自然沉淀。
第二阶段:正常使用期(第 2-3 天)
- 分散式浏览视频
每天分 3-4 次通过 ixBrowser 打开账号,每次停留 10-20 分钟,浏览系统推荐的不同类型视频。 - 自然互动,拒绝机械化
- 点赞:每天 5-10 个,避免连续点赞;
- 评论:每天 1-3 条原创短句(如 “这个方法好实用!”),不复制粘贴;
- 关注:每天 1-3 个同领域账号。
ixBrowser 的 “窗口同步功能” ,可设置鼠标点击延迟,仿真输入操作,避免冗杂重复的养号工作。
- 保持操作随机性
避免固定时间段操作,模拟真实用户的碎片化使用习惯。
第三阶段:轻度内容参与(第 4-5 天)
- 提升互动强度
点赞数可增至 10-15 个 / 天,评论和关注频率保持稳定。 - 发布轻量非营销内容
发布 1-2 条与账号定位相关的内容(如美食账号发家常菜片段、旅行账号发风景视频),不包含广告或外部链接。 - 测试系统反馈
观察视频播放量和互动率,若单条视频播放量超过 500、互动率(点赞 + 评论 / 播放)>3%,说明账号已获得初步推荐。
第四阶段:逐步提升活跃度(第 6 天及以后)
- 规律发布内容
逐步增加至每天 1 条内容,避免短时间内密集发布。 - 深化互动与话题参与
积极回复评论区留言,提升账号社交属性;参与热门话题(Hashtag Challenge),增加曝光机会。 - 维持账号稳定性
保持固定的使用频率(如每天总时长 30-60 分钟),避免突然高频操作或长期不活跃。
批量养号的核心挑战与 ixBrowser 的解决方案
批量养号的难点在于 “多账号独立化”,而 ixBrowser 通过以下功能精准破解:1.账号关联风险(共享设备 / IP)
生成独立设备指纹(包括浏览器版本、字体、时区等),每个账号绑定专属代理 IP,实现设备与网络环境完全隔离;
2.网络环境频繁变更引发账号异常
批量运营账号时,常需频繁切换登录节点,如更换代理IP或跨地区接入,导致账号网络环境不稳定。TikTok平台会对异常登录行为进行实时监测,若检测到IP地址短时间内多次变动,系统可能判定为盗号或异常操作,从而触发验证机制,要求输入验证码,甚至临时封禁账号。
3.操作行为模式化,易被识别为机器行为
若同一批账号在日常操作中呈现高度一致性——如在相同时段观看同类视频、点赞数相近、评论内容雷同等,TikTok算法极易将其归类为“批量操作”或机器人账号。平台会综合分析账号行为特征,包括登录频率、使用时长、互动行为等维度。一旦多个账号行为轨迹高度重合,便会触发风控机制,导致账号受限。
4.多账号管理复杂,运营成本高昂
批量运营账号不仅涉及多账号切换,更包括以下高阶管理任务:
-
跟踪各账号成长进度
-
实时监测账号安全状态(是否出现异常提示、流量受限等)
-
为不同账号分配独立网络及设备环境
若仅依靠人工手动切换账号,不仅效率低下,还极易因操作失误造成账号混淆,增加运营风险。
用 ixBrowser 实现批量养号
- 创建独立浏览器环境
ixBrowser支持多浏览器环境创建,轻松满足不同养号需求。
- 绑定独立代理IP
可以为每个浏览器环境配置独立代理IP,同时ixBrowser集成了优质的代理服务商资源,保证IP与目标市场匹配,避免IP异常风险。
- 批量账号登录管理
AdsPower支持一键批量登录多个TikTok账号,无需手动重复输入密码,提高登录效率。
- 窗口同步
多窗口同步刷视频、点赞、关注、评论等动作养号更加高效。
- 多账号分组管理
支持账号分类管理,便于不同项目、市场、团队成员协同操作,提升运营效率。

June 17 2025
2025 Best 10 Proxy Providers
Proxy services have become indispensable in today's world and people are using proxies to fulfill their diverse needs. Individuals use proxies to access content with geo-network restrictions, enhance personal privacy, and bypass website blocks. Businesses use proxies for web scraping and market research.
There are many proxy service providers on the market, and it is particularly important to choose a trustworthy service provider. Today we will conduct a simple analysis and list the 10 best proxy service providers in 2025.
#1
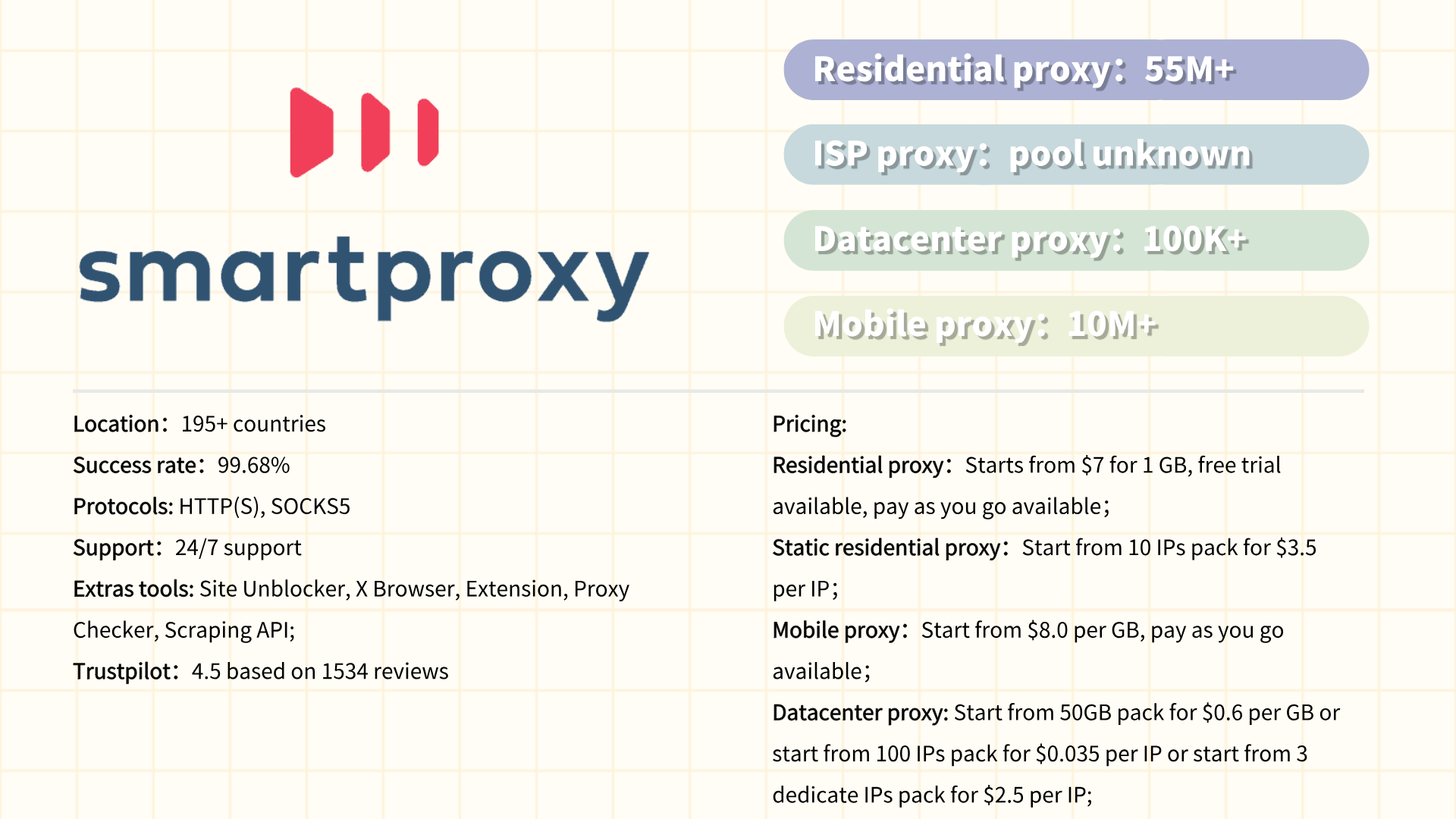
Smartproxy is a leading proxy service provider offering residential, datacenter, and mobile proxies to empower businesses and individuals in managing web data collection, ad verification, SEO monitoring, and bypassing geo-restrictions. With a global network of over 55 million IPs across 195+ locations, it ensures high anonymity, fast speeds, and reliable connectivity. Its user-friendly dashboard, flexible pricing tiers, and API integration cater to both small-scale projects and enterprise-level operations. Smartproxy emphasizes ethical sourcing of residential IPs and compliance with data privacy regulations, making it a trusted choice for market research, e-commerce, and cybersecurity applications.
Pros:
·Extensive IP pool with global coverage.
·Intuitive interface and 24/7 customer support.
·Competitive pricing for small to medium users.
·Strong focus on ethical proxy sourcing.
·Supports multiple protocols (HTTP/S, SOCKS5).
Cons:
·Speed inconsistencies during peak hours.
·Limited advanced customization for enterprise clients.
·Fewer mobile proxy locations compared to competitors.
Smartproxy special offer:
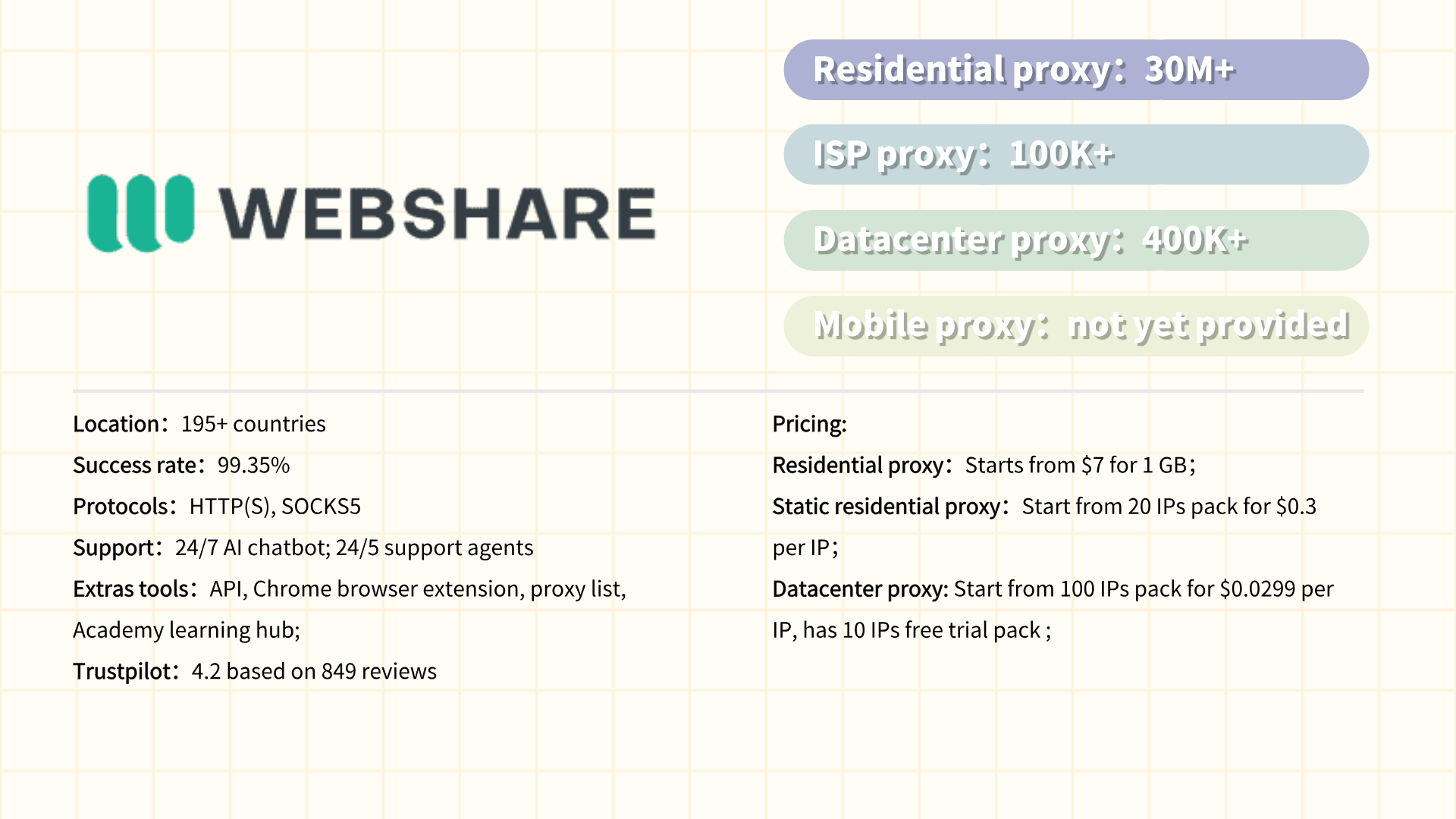
Webshare is a cost-effective proxy service provider specializing in residential and datacenter proxies, designed to support web scraping, data mining, and anonymity-focused tasks. Known for its simplicity and affordability, Webshare offers a global network of IPs across 195+ locations, with flexible plans catering to individuals, developers, and small-to-medium businesses. Its proxies support HTTP/S and SOCKS5 protocols, and the platform emphasizes ease of use through features like automatic IP rotation, API access, and a user-friendly dashboard. Webshare is particularly popular for its transparent pricing, free tier (limited IPs), and pay-as-you-go options, making it accessible for testing or low-budget projects. While it lacks enterprise-grade tools, it remains a practical choice for basic data collection, SEO monitoring, and bypassing geo-blocks.
Pros:
·Affordable pricing with free tier and scalable pay-as-you-go plans.
·Simple setup and intuitive interface for non-technical users.
·Flexible authentication (IP whitelist, username/password).
·Supports multiple protocols (HTTP/S, SOCKS5).
·Transparent service with no hidden fees.
Cons:
·Smaller IP pool compared to premium competitors.
·Basic features lacking advanced anti-blocking or AI-powered tools.
·Inconsistent speeds for high-demand regions.
Webshare special offer:
#3
Oxylabs is a premium proxy and web scraping solutions provider, catering primarily to enterprises and developers requiring large-scale data collection capabilities. Renowned for its robust infrastructure, Oxylabs offers residential, datacenter, and mobile proxies, alongside specialized tools like Next-Gen Web Scraper and SERP Scraping API. Its network spans over 100 million residential IPs across 195+ regions, ensuring high anonymity, granular targeting, and exceptional success rates for tasks such as price monitoring, market research, and competitive analysis. Oxylabs emphasizes compliance with global data regulations (e.g., GDPR) and ethical proxy sourcing, positioning itself as a go-to solution for industries like e-commerce, finance, and cybersecurity. With advanced features like AI-powered anti-blocking technology and 24/7 technical support, it prioritizes scalability and reliability for complex data operations.
Pros:
·Massive, ethically sourced IP pool with unmatched geographic diversity.
·Enterprise-grade tools for high-volume, complex scraping tasks.
·Advanced anti-detection mechanisms and high success rates.
·Dedicated account managers and responsive customer support.
·Strong compliance with data privacy standards.
Cons:
·Premium pricing, less accessible for small businesses or individual users.
·Steeper learning curve for non-technical users due to advanced features.
·Occasional delays in proxy rotation during high-demand periods.
·Limited flexibility in pricing plans compared to budget competitors.
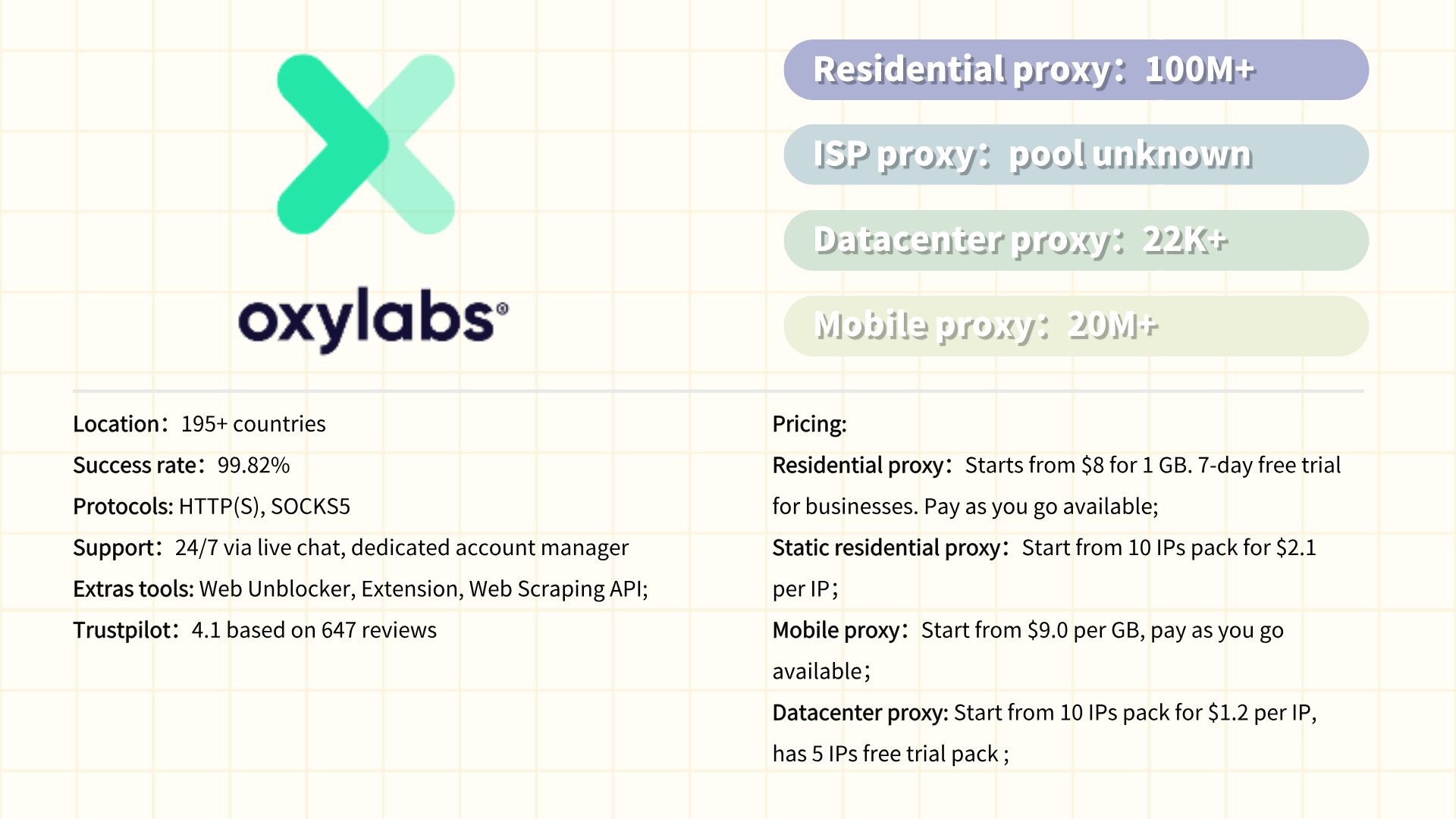
#4 Bright Data
Bright Data is a globally recognized leader in proxy services and web data collection solutions, trusted by enterprises, researchers, and developers for large-scale, reliable data acquisition. Formerly known as Luminati Networks, the platform offers a comprehensive suite of proxies, including residential, datacenter, mobile, and ISP proxies, supported by one of the world’s largest ethically sourced IP networks (over 72 million IPs across 195+ countries). Its infrastructure enables advanced use cases such as ad fraud detection, e-commerce price monitoring, market trend analysis, and SEO optimization. Bright Data emphasizes compliance with GDPR, CCPA, and other data privacy regulations, ensuring ethical data collection practices. The platform also provides developer-friendly tools like a browser extension, APIs, and a user-friendly dashboard, along with AI-powered anti-blocking technology to bypass CAPTCHAs and IP bans.
Pros:
·Unparalleled IP diversity and global coverage for granular targeting.
·Ethically sourced residential IPs with full compliance and transparency.
·High success rates and advanced anti-detection features (e.g., AI-powered tools).
·Robust infrastructure tailored for enterprise-level scalability and reliability.
·Comprehensive toolset (APIs, browser extensions, proxy manager) for developers.
·24/7 enterprise-grade support and dedicated account management.
Cons:
·Premium pricing model, making it cost-prohibitive for small businesses or individual users.
·Complex setup for non-technical users due to advanced customization options.
·Occasional latency issues in high-demand geolocations.
·Strict compliance checks may delay onboarding for some clients.
·Limited pay-as-you-go options compared to budget competitors.
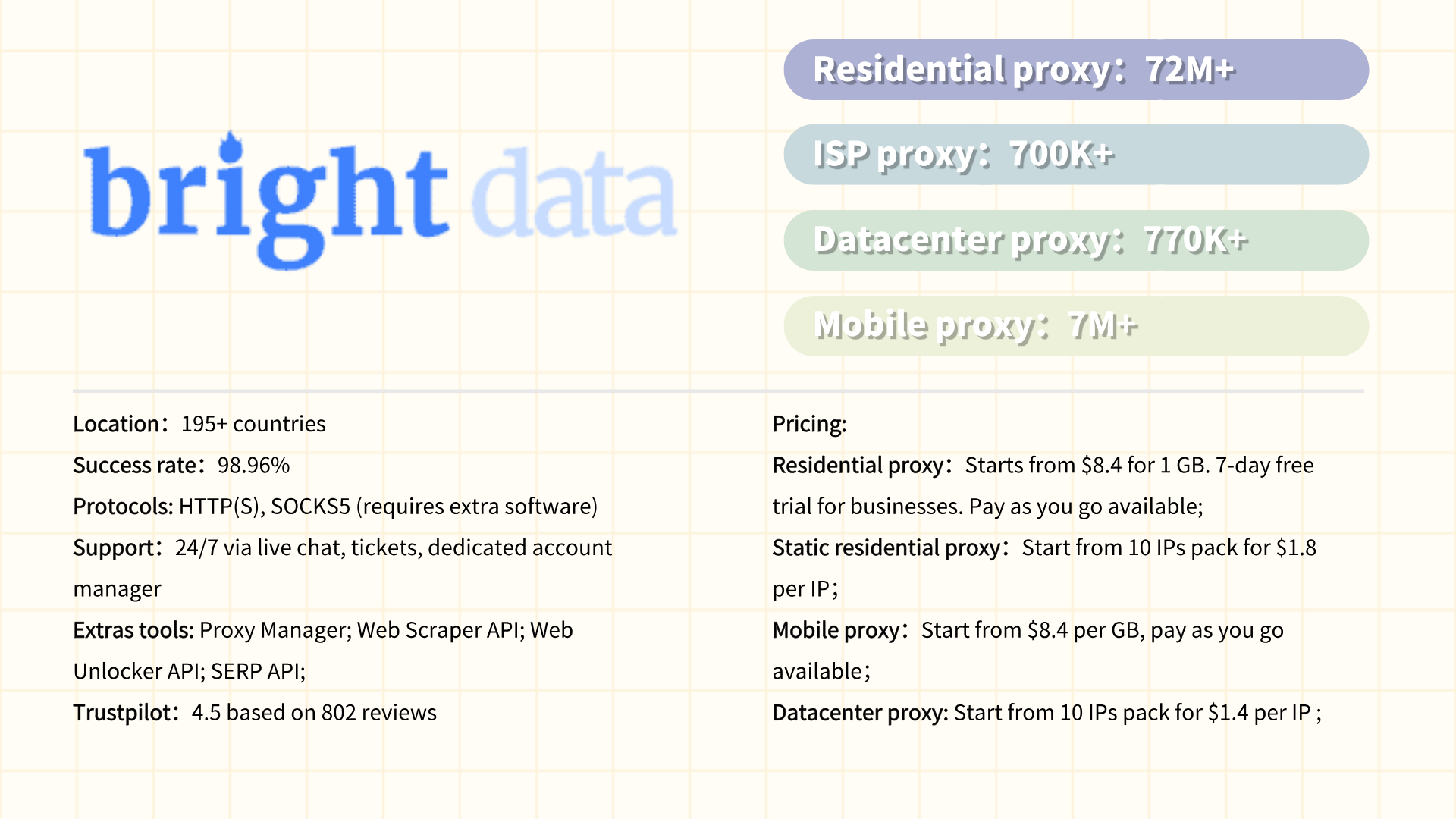
#5 SOAX
SOAX is a proxy service provider specializing in residential and mobile proxies, designed to support data scraping, ad verification, and market research. With a focus on flexibility and affordability, SOAX offers a global network of over 10 million IPs across 150+ locations, emphasizing ethical sourcing and dynamic IP rotation to minimize blocking risks. The platform caters to developers, marketers, and businesses seeking scalable solutions for tasks like competitor analysis, price monitoring, and social media management. SOAX stands out for its user-friendly dashboard, granular targeting options (e.g., country, city, or ISP filters), and customizable plans, including pay-as-you-go pricing. While less enterprise-oriented than premium competitors, it balances cost and functionality for mid-sized projects, prioritizing ease of integration via API and proxy management tools.
Pros:
·Dynamic IP rotation and targeting by location/ISP to reduce blocking.
·Ethically sourced residential proxies with transparent practices.
·Simple interface and quick setup for non-technical users.
·API integration and detailed usage statistics.
Cons:
·Limited advanced features (e.g., no AI anti-detection tools).
·Inconsistent speeds in high-demand regions.
·Basic customer support (no 24/7 live assistance).
·Mobile proxy coverage lags behind premium competitors.
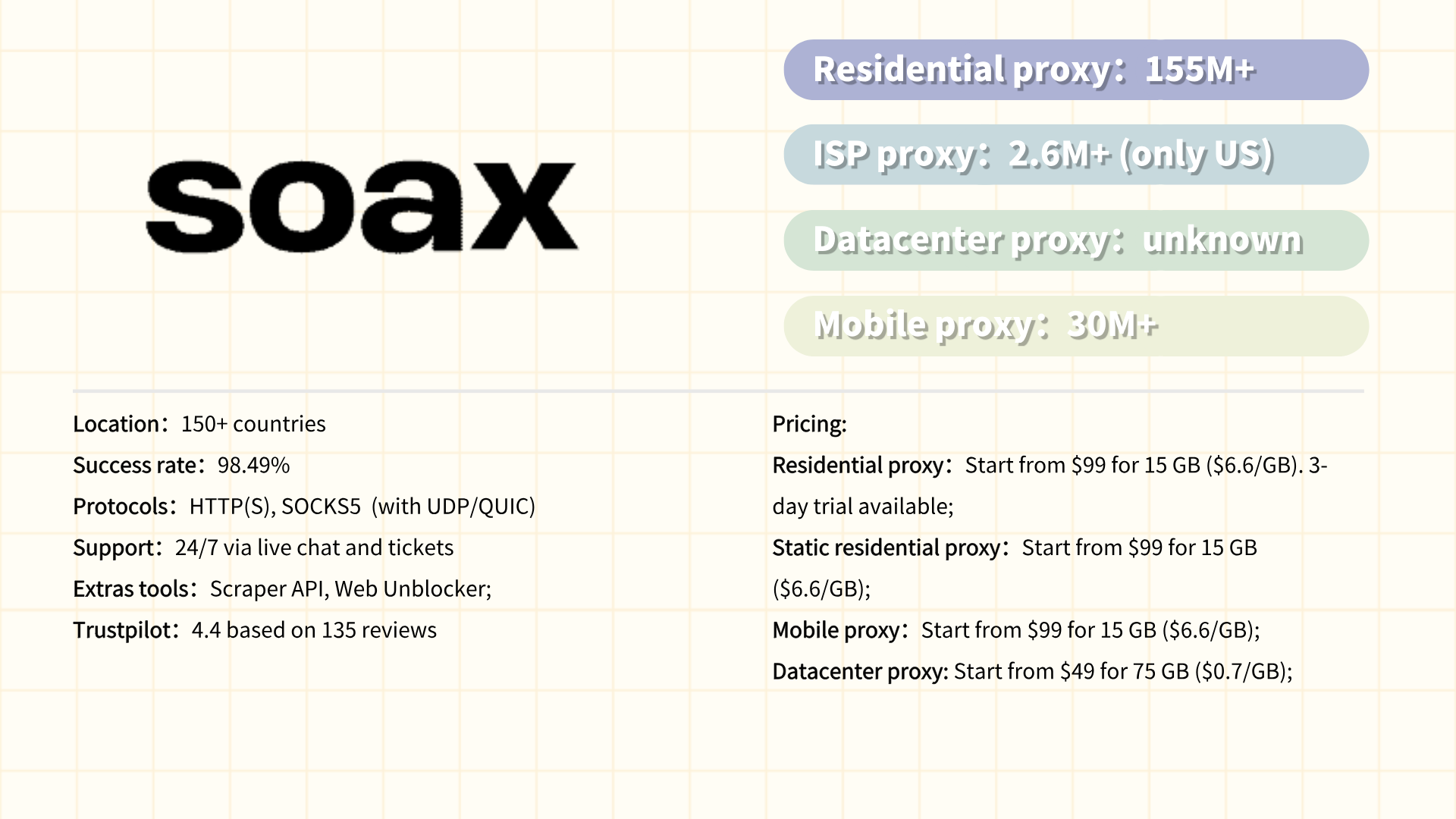
#6 IPRoyal
IPRoyal is a proxy service provider offering residential, datacenter, and sneaker proxies tailored for web scraping, e-commerce automation, and bypassing geo-restrictions. Known for its budget-friendly approach, IPRoyal emphasizes simplicity and accessibility, making it a popular choice for individuals, developers, and small businesses. Its residential proxy network spans millions of IPs across 195+ regions, with a focus on ethical sourcing through a user-approved "Paid Proxy" model, where individuals voluntarily share their idle bandwidth. The platform supports HTTP/S and SOCKS5 protocols and provides features like automatic IP rotation, session control, and targeting by country or city. IPRoyal’s straightforward pricing, transparent policies, and user-friendly dashboard cater to users seeking cost-effective solutions for tasks like SEO monitoring, ad verification, and social media management.
Pros:
·Affordable pricing with flexible pay-as-you-go and subscription plans.
·Ethically sourced residential proxies via a consent-based network.
·Easy-to-use interface and quick integration for non-technical users.
·Global coverage (195+ countries) with city-level targeting.
·Transparent policies and no hidden fees.
Cons:
·Smaller IP pool compared to premium competitors like Bright Data or Oxylabs.
·Limited advanced features (e.g., no AI-powered anti-blocking tools).
·Inconsistent speeds during peak usage times.
·Fewer customization options for enterprise-level needs.
#7 NetNut
NetNut is a proxy service provider specializing in high-speed ISP (Internet Service Provider) proxies, designed for large-scale web scraping, ad verification, and e-commerce automation. Unlike traditional residential or datacenter proxies, NetNut leverages a unique ISP-based infrastructure to deliver faster speeds, lower latency, and higher reliability for data-intensive tasks. Its network routes traffic through direct ISP partnerships, ensuring minimal blocking and near-instantaneous response times for applications like price monitoring, SEO tracking, and inventory management. NetNut emphasizes scalability, offering unlimited concurrent sessions and a global network spanning 100+ countries. The platform caters to enterprises and developers seeking compliance-focused solutions, with features like granular geo-targeting, rotating IPs, and integration via API or proxy manager tools. Its transparent pricing and focus on performance make it a competitive choice for businesses prioritizing speed and stability over residential IP diversity.
Pros:
·Blazing-fast speeds due to ISP-based network architecture.
·High reliability and low latency for real-time data scraping.
·Unlimited concurrent sessions and scalable for enterprise needs.
·Simple integration with APIs, browser extensions, and third-party tools.
·Strong compliance with ethical data collection standards.
Cons:
·Limited IP diversity compared to residential proxy providers.
·Higher cost for small-scale users or short-term projects.
·Fewer targeting options (e.g., no city-level precision in some regions).
·Basic customer support for non-enterprise clients.
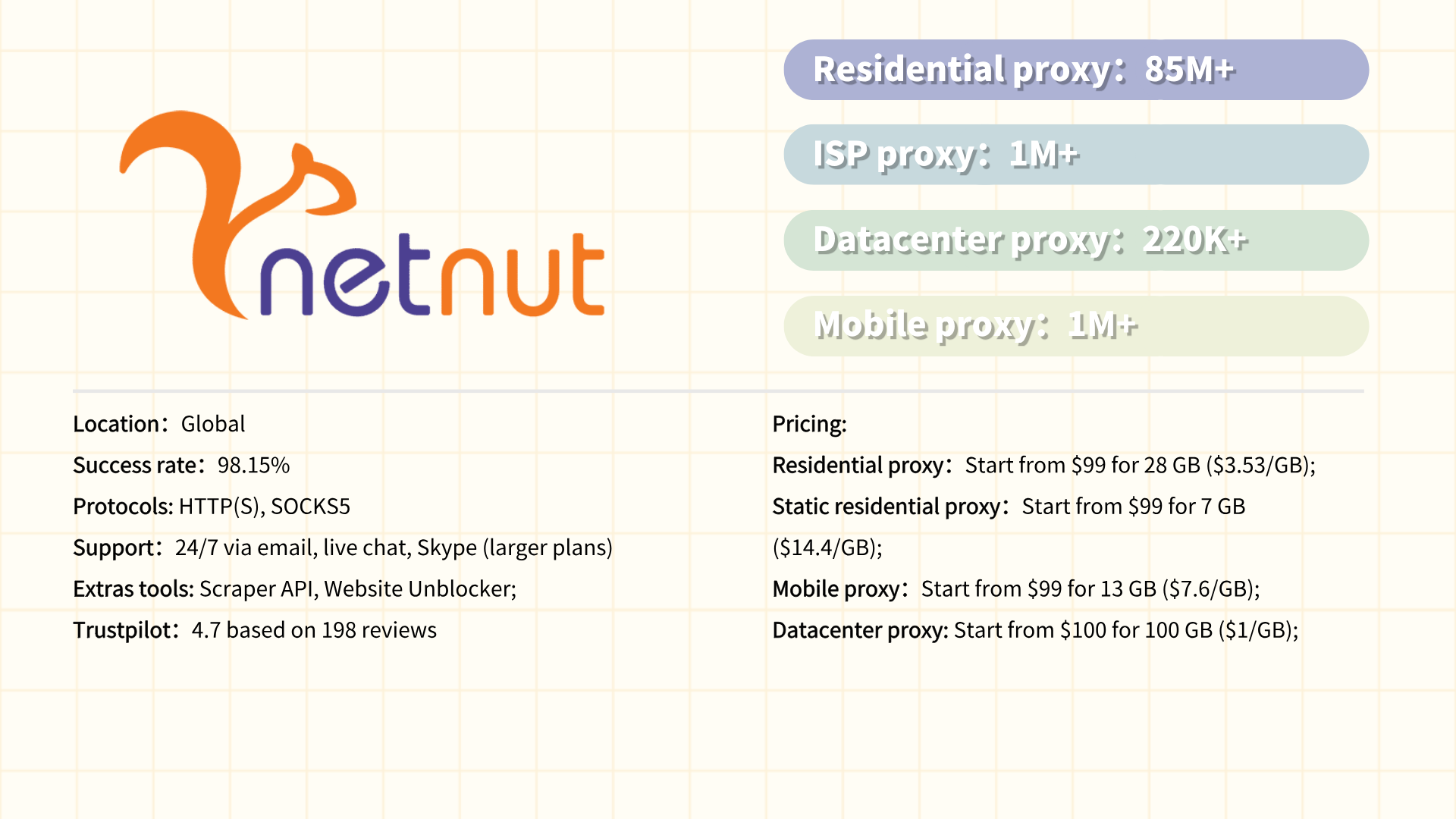
#8 DataImpulse
DataImpulse is a proxy and web data collection platform designed to empower businesses with reliable access to public web data for market research, competitive analysis, and automation tasks. Specializing in residential and datacenter proxies, DataImpulse offers a global network of IPs with granular geo-targeting capabilities, enabling users to bypass geo-blocks, scrape data efficiently, and monitor trends anonymously. The platform emphasizes ease of use, featuring a streamlined dashboard, API integration, and tools for IP rotation and session management. Tailored for startups and mid-sized enterprises, DataImpulse focuses on affordability without compromising core functionalities like ad verification, SEO tracking, and e-commerce price aggregation. While smaller in scale compared to industry giants, it prioritizes ethical data practices and transparent pricing models.
Pros:
·Cost-effective plans for small businesses or budget-conscious users.
·User-friendly interface with quick setup for non-technical users.
·Flexible geo-targeting (country/city-level) for precise data collection.
·Ethical IP sourcing and compliance with basic data privacy standards.
·API support and integration with popular scraping tools.
Cons:
·Limited IP pool size compared to leading competitors.
·No ISP proxy types.
·Basic anti-blocking features, leading to higher detection risks for complex tasks.
·Inconsistent speeds in high-demand regions.
·Limited customer support.
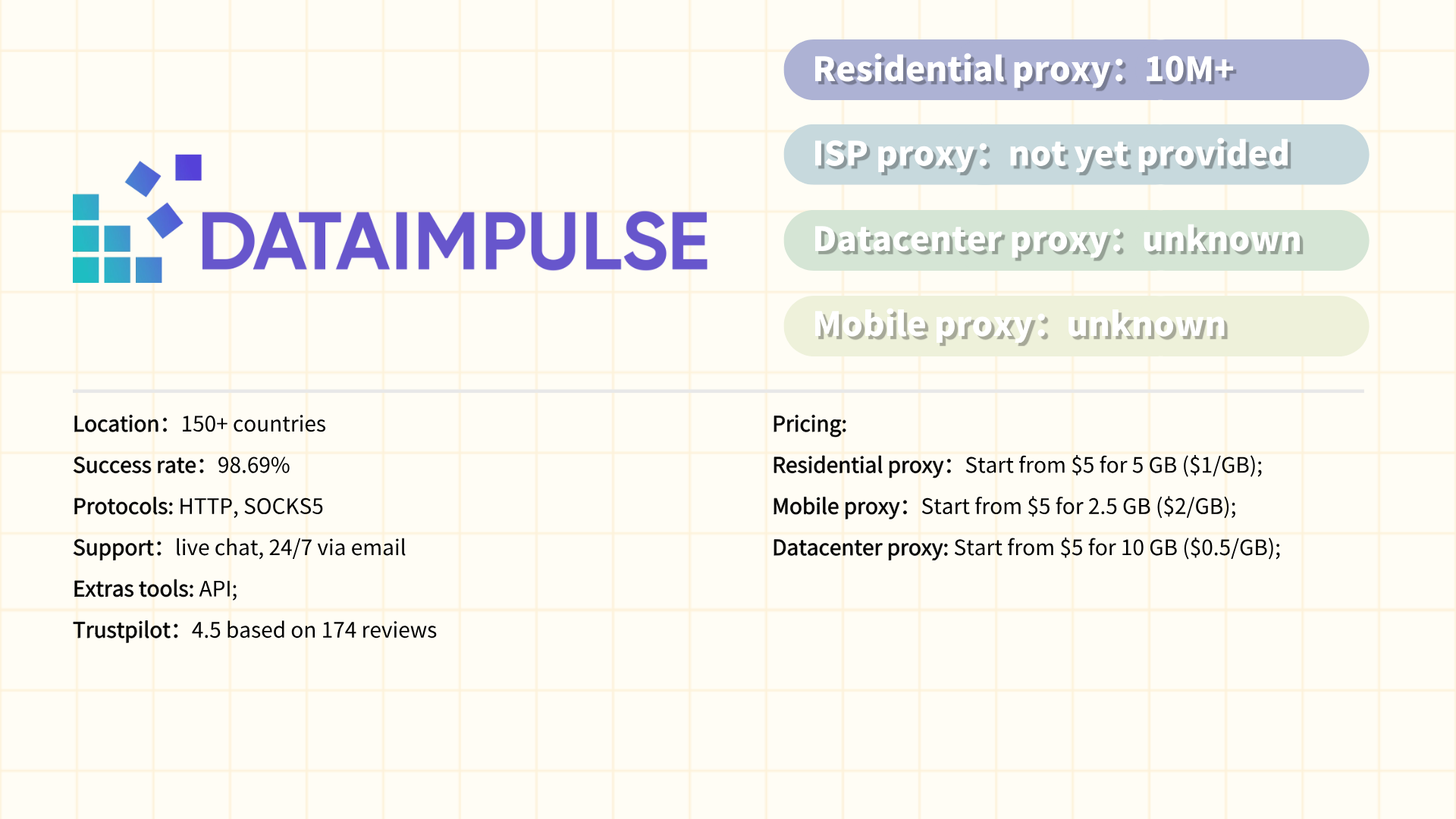
#9 MarsProxies
MarsProxies is a proxy service provider offering residential, datacenter, and ISP proxies tailored for web scraping, ad verification, and bypassing geo-restrictions. Designed for businesses and developers, MarsProxies emphasizes speed and reliability, leveraging a global network of ethically sourced IPs across 195+ countries. Its infrastructure supports high-volume data extraction, SEO monitoring, and e-commerce automation, with features like automatic IP rotation, session control, and granular geo-targeting (country/city-level). The platform caters to both small-scale projects and enterprise needs through flexible pricing tiers, API integration, and compatibility with HTTP/S and SOCKS5 protocols. MarsProxies prioritizes user-friendliness, offering a streamlined dashboard and 24/7 customer support, while maintaining compliance with data privacy regulations like GDPR.
Pros:
·High-speed proxies optimized for real-time data scraping and automation.
·Ethically sourced IPs with global coverage (195+ countries).
·User-friendly interface and easy integration via API or proxy managers.
·Flexible pricing (pay-as-you-go and subscription plans).
·Strong uptime and reliability for mission-critical tasks.
Cons:
·Limited IP pool diversity compared to industry leaders like Bright Data.
·Basic anti-detection tools (lacks AI-powered solutions for bypassing advanced blocks).
·Inconsistent customer support response times for non-enterprise users.
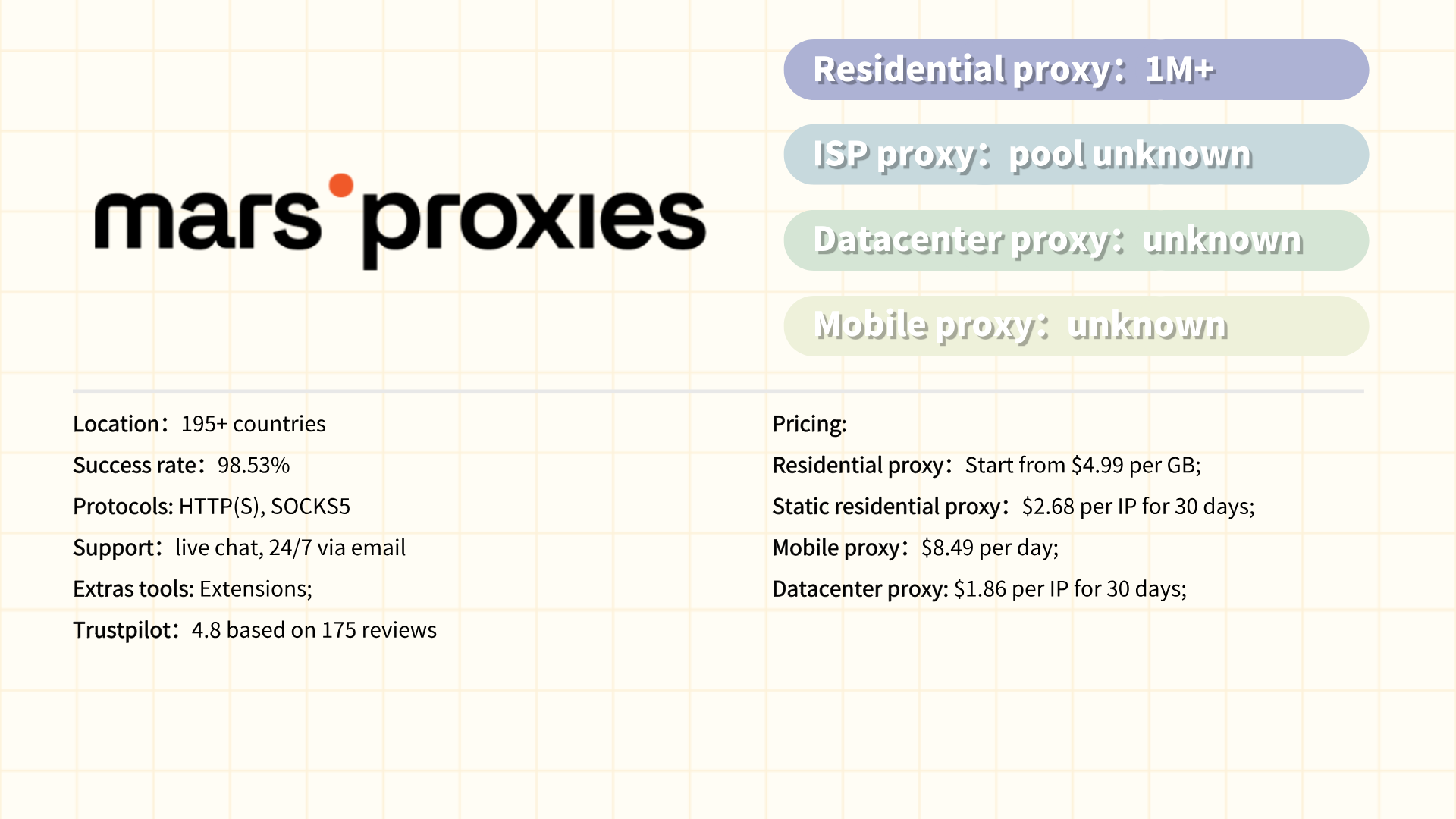
#10 Infatica
Infatica is a proxy service provider specializing in ethically sourced residential and datacenter proxies, designed to support web scraping, ad verification, and data aggregation tasks. With a focus on compliance and transparency, Infatica offers a global network of over 15 million IPs across 190+ countries, leveraging partnerships with internet service providers (ISPs) to ensure high-speed, low-latency connections. The platform caters to businesses and developers requiring reliable geo-targeting, IP rotation, and session management for use cases like price monitoring, market research, and SEO tracking. Infatica emphasizes ethical proxy sourcing through user consent and adherence to GDPR and other privacy regulations. Its user-friendly dashboard, API integration, and flexible pricing plans (including pay-as-you-go options) make it accessible to both small-scale projects and enterprise clients.
Pros:
·Ethically sourced residential proxies with ISP partnerships for high legitimacy.
·Global coverage (190+ countries) and city-level targeting capabilities.
·High-speed connections optimized for real-time data scraping.
·Transparent pricing with scalable plans for diverse budgets.
·Strong compliance focus (GDPR, CCPA) and anti-abuse mechanisms.
Cons:
·Smaller IP pool compared to industry giants like Bright Data or Oxylabs.
·Limited advanced features (e.g., no AI-powered anti-detection tools).
·Inconsistent availability in niche or low-demand regions.
·Basic customer support.
There are many proxy service providers on the market, and it is particularly important to choose a trustworthy service provider. Today we will conduct a simple analysis and list the 10 best proxy service providers in 2025.
#1
Smartproxy
Smartproxy is a leading proxy service provider offering residential, datacenter, and mobile proxies to empower businesses and individuals in managing web data collection, ad verification, SEO monitoring, and bypassing geo-restrictions. With a global network of over 55 million IPs across 195+ locations, it ensures high anonymity, fast speeds, and reliable connectivity. Its user-friendly dashboard, flexible pricing tiers, and API integration cater to both small-scale projects and enterprise-level operations. Smartproxy emphasizes ethical sourcing of residential IPs and compliance with data privacy regulations, making it a trusted choice for market research, e-commerce, and cybersecurity applications.
Pros:
·Extensive IP pool with global coverage.
·Intuitive interface and 24/7 customer support.
·Competitive pricing for small to medium users.
·Strong focus on ethical proxy sourcing.
·Supports multiple protocols (HTTP/S, SOCKS5).
Cons:
·Speed inconsistencies during peak hours.
·Limited advanced customization for enterprise clients.
·Fewer mobile proxy locations compared to competitors.
Smartproxy special offer:
Smartproxy residential proxies are currently at 40% off using the code RESI40

#2 Webshare
Webshare is a cost-effective proxy service provider specializing in residential and datacenter proxies, designed to support web scraping, data mining, and anonymity-focused tasks. Known for its simplicity and affordability, Webshare offers a global network of IPs across 195+ locations, with flexible plans catering to individuals, developers, and small-to-medium businesses. Its proxies support HTTP/S and SOCKS5 protocols, and the platform emphasizes ease of use through features like automatic IP rotation, API access, and a user-friendly dashboard. Webshare is particularly popular for its transparent pricing, free tier (limited IPs), and pay-as-you-go options, making it accessible for testing or low-budget projects. While it lacks enterprise-grade tools, it remains a practical choice for basic data collection, SEO monitoring, and bypassing geo-blocks.
Pros:
·Affordable pricing with free tier and scalable pay-as-you-go plans.
·Simple setup and intuitive interface for non-technical users.
·Flexible authentication (IP whitelist, username/password).
·Supports multiple protocols (HTTP/S, SOCKS5).
·Transparent service with no hidden fees.
Cons:
·Smaller IP pool compared to premium competitors.
·Basic features lacking advanced anti-blocking or AI-powered tools.
·Inconsistent speeds for high-demand regions.
Webshare special offer:
Create a new account
and receive "10 free datacenter proxies + 1GB/month of bandwidth to use as long as you want, no credit card required"
#3
Oxylabs
Oxylabs is a premium proxy and web scraping solutions provider, catering primarily to enterprises and developers requiring large-scale data collection capabilities. Renowned for its robust infrastructure, Oxylabs offers residential, datacenter, and mobile proxies, alongside specialized tools like Next-Gen Web Scraper and SERP Scraping API. Its network spans over 100 million residential IPs across 195+ regions, ensuring high anonymity, granular targeting, and exceptional success rates for tasks such as price monitoring, market research, and competitive analysis. Oxylabs emphasizes compliance with global data regulations (e.g., GDPR) and ethical proxy sourcing, positioning itself as a go-to solution for industries like e-commerce, finance, and cybersecurity. With advanced features like AI-powered anti-blocking technology and 24/7 technical support, it prioritizes scalability and reliability for complex data operations.
Pros:
·Massive, ethically sourced IP pool with unmatched geographic diversity.
·Enterprise-grade tools for high-volume, complex scraping tasks.
·Advanced anti-detection mechanisms and high success rates.
·Dedicated account managers and responsive customer support.
·Strong compliance with data privacy standards.
Cons:
·Premium pricing, less accessible for small businesses or individual users.
·Steeper learning curve for non-technical users due to advanced features.
·Occasional delays in proxy rotation during high-demand periods.
·Limited flexibility in pricing plans compared to budget competitors.

#4 Bright Data
Bright Data is a globally recognized leader in proxy services and web data collection solutions, trusted by enterprises, researchers, and developers for large-scale, reliable data acquisition. Formerly known as Luminati Networks, the platform offers a comprehensive suite of proxies, including residential, datacenter, mobile, and ISP proxies, supported by one of the world’s largest ethically sourced IP networks (over 72 million IPs across 195+ countries). Its infrastructure enables advanced use cases such as ad fraud detection, e-commerce price monitoring, market trend analysis, and SEO optimization. Bright Data emphasizes compliance with GDPR, CCPA, and other data privacy regulations, ensuring ethical data collection practices. The platform also provides developer-friendly tools like a browser extension, APIs, and a user-friendly dashboard, along with AI-powered anti-blocking technology to bypass CAPTCHAs and IP bans.
Pros:
·Unparalleled IP diversity and global coverage for granular targeting.
·Ethically sourced residential IPs with full compliance and transparency.
·High success rates and advanced anti-detection features (e.g., AI-powered tools).
·Robust infrastructure tailored for enterprise-level scalability and reliability.
·Comprehensive toolset (APIs, browser extensions, proxy manager) for developers.
·24/7 enterprise-grade support and dedicated account management.
Cons:
·Premium pricing model, making it cost-prohibitive for small businesses or individual users.
·Complex setup for non-technical users due to advanced customization options.
·Occasional latency issues in high-demand geolocations.
·Strict compliance checks may delay onboarding for some clients.
·Limited pay-as-you-go options compared to budget competitors.

#5 SOAX
SOAX is a proxy service provider specializing in residential and mobile proxies, designed to support data scraping, ad verification, and market research. With a focus on flexibility and affordability, SOAX offers a global network of over 10 million IPs across 150+ locations, emphasizing ethical sourcing and dynamic IP rotation to minimize blocking risks. The platform caters to developers, marketers, and businesses seeking scalable solutions for tasks like competitor analysis, price monitoring, and social media management. SOAX stands out for its user-friendly dashboard, granular targeting options (e.g., country, city, or ISP filters), and customizable plans, including pay-as-you-go pricing. While less enterprise-oriented than premium competitors, it balances cost and functionality for mid-sized projects, prioritizing ease of integration via API and proxy management tools.
Pros:
·Dynamic IP rotation and targeting by location/ISP to reduce blocking.
·Ethically sourced residential proxies with transparent practices.
·Simple interface and quick setup for non-technical users.
·API integration and detailed usage statistics.
Cons:
·Limited advanced features (e.g., no AI anti-detection tools).
·Inconsistent speeds in high-demand regions.
·Basic customer support (no 24/7 live assistance).
·Mobile proxy coverage lags behind premium competitors.

#6 IPRoyal
IPRoyal is a proxy service provider offering residential, datacenter, and sneaker proxies tailored for web scraping, e-commerce automation, and bypassing geo-restrictions. Known for its budget-friendly approach, IPRoyal emphasizes simplicity and accessibility, making it a popular choice for individuals, developers, and small businesses. Its residential proxy network spans millions of IPs across 195+ regions, with a focus on ethical sourcing through a user-approved "Paid Proxy" model, where individuals voluntarily share their idle bandwidth. The platform supports HTTP/S and SOCKS5 protocols and provides features like automatic IP rotation, session control, and targeting by country or city. IPRoyal’s straightforward pricing, transparent policies, and user-friendly dashboard cater to users seeking cost-effective solutions for tasks like SEO monitoring, ad verification, and social media management.
Pros:
·Affordable pricing with flexible pay-as-you-go and subscription plans.
·Ethically sourced residential proxies via a consent-based network.
·Easy-to-use interface and quick integration for non-technical users.
·Global coverage (195+ countries) with city-level targeting.
·Transparent policies and no hidden fees.
Cons:
·Smaller IP pool compared to premium competitors like Bright Data or Oxylabs.
·Limited advanced features (e.g., no AI-powered anti-blocking tools).
·Inconsistent speeds during peak usage times.
·Fewer customization options for enterprise-level needs.

#7 NetNut
NetNut is a proxy service provider specializing in high-speed ISP (Internet Service Provider) proxies, designed for large-scale web scraping, ad verification, and e-commerce automation. Unlike traditional residential or datacenter proxies, NetNut leverages a unique ISP-based infrastructure to deliver faster speeds, lower latency, and higher reliability for data-intensive tasks. Its network routes traffic through direct ISP partnerships, ensuring minimal blocking and near-instantaneous response times for applications like price monitoring, SEO tracking, and inventory management. NetNut emphasizes scalability, offering unlimited concurrent sessions and a global network spanning 100+ countries. The platform caters to enterprises and developers seeking compliance-focused solutions, with features like granular geo-targeting, rotating IPs, and integration via API or proxy manager tools. Its transparent pricing and focus on performance make it a competitive choice for businesses prioritizing speed and stability over residential IP diversity.
Pros:
·Blazing-fast speeds due to ISP-based network architecture.
·High reliability and low latency for real-time data scraping.
·Unlimited concurrent sessions and scalable for enterprise needs.
·Simple integration with APIs, browser extensions, and third-party tools.
·Strong compliance with ethical data collection standards.
Cons:
·Limited IP diversity compared to residential proxy providers.
·Higher cost for small-scale users or short-term projects.
·Fewer targeting options (e.g., no city-level precision in some regions).
·Basic customer support for non-enterprise clients.

#8 DataImpulse
DataImpulse is a proxy and web data collection platform designed to empower businesses with reliable access to public web data for market research, competitive analysis, and automation tasks. Specializing in residential and datacenter proxies, DataImpulse offers a global network of IPs with granular geo-targeting capabilities, enabling users to bypass geo-blocks, scrape data efficiently, and monitor trends anonymously. The platform emphasizes ease of use, featuring a streamlined dashboard, API integration, and tools for IP rotation and session management. Tailored for startups and mid-sized enterprises, DataImpulse focuses on affordability without compromising core functionalities like ad verification, SEO tracking, and e-commerce price aggregation. While smaller in scale compared to industry giants, it prioritizes ethical data practices and transparent pricing models.
Pros:
·Cost-effective plans for small businesses or budget-conscious users.
·User-friendly interface with quick setup for non-technical users.
·Flexible geo-targeting (country/city-level) for precise data collection.
·Ethical IP sourcing and compliance with basic data privacy standards.
·API support and integration with popular scraping tools.
Cons:
·Limited IP pool size compared to leading competitors.
·No ISP proxy types.
·Basic anti-blocking features, leading to higher detection risks for complex tasks.
·Inconsistent speeds in high-demand regions.
·Limited customer support.

#9 MarsProxies
MarsProxies is a proxy service provider offering residential, datacenter, and ISP proxies tailored for web scraping, ad verification, and bypassing geo-restrictions. Designed for businesses and developers, MarsProxies emphasizes speed and reliability, leveraging a global network of ethically sourced IPs across 195+ countries. Its infrastructure supports high-volume data extraction, SEO monitoring, and e-commerce automation, with features like automatic IP rotation, session control, and granular geo-targeting (country/city-level). The platform caters to both small-scale projects and enterprise needs through flexible pricing tiers, API integration, and compatibility with HTTP/S and SOCKS5 protocols. MarsProxies prioritizes user-friendliness, offering a streamlined dashboard and 24/7 customer support, while maintaining compliance with data privacy regulations like GDPR.
Pros:
·High-speed proxies optimized for real-time data scraping and automation.
·Ethically sourced IPs with global coverage (195+ countries).
·User-friendly interface and easy integration via API or proxy managers.
·Flexible pricing (pay-as-you-go and subscription plans).
·Strong uptime and reliability for mission-critical tasks.
Cons:
·Limited IP pool diversity compared to industry leaders like Bright Data.
·Basic anti-detection tools (lacks AI-powered solutions for bypassing advanced blocks).
·Inconsistent customer support response times for non-enterprise users.

#10 Infatica
Infatica is a proxy service provider specializing in ethically sourced residential and datacenter proxies, designed to support web scraping, ad verification, and data aggregation tasks. With a focus on compliance and transparency, Infatica offers a global network of over 15 million IPs across 190+ countries, leveraging partnerships with internet service providers (ISPs) to ensure high-speed, low-latency connections. The platform caters to businesses and developers requiring reliable geo-targeting, IP rotation, and session management for use cases like price monitoring, market research, and SEO tracking. Infatica emphasizes ethical proxy sourcing through user consent and adherence to GDPR and other privacy regulations. Its user-friendly dashboard, API integration, and flexible pricing plans (including pay-as-you-go options) make it accessible to both small-scale projects and enterprise clients.
Pros:
·Ethically sourced residential proxies with ISP partnerships for high legitimacy.
·Global coverage (190+ countries) and city-level targeting capabilities.
·High-speed connections optimized for real-time data scraping.
·Transparent pricing with scalable plans for diverse budgets.
·Strong compliance focus (GDPR, CCPA) and anti-abuse mechanisms.
Cons:
·Smaller IP pool compared to industry giants like Bright Data or Oxylabs.
·Limited advanced features (e.g., no AI-powered anti-detection tools).
·Inconsistent availability in niche or low-demand regions.
·Basic customer support.


May 29 2025
How to setup Proxy 302 with ixBrowser (如何在ixBrowser中配置Proxy302代理)
What is Proxy302?
Proxy302 是什么?
Proxy302
is a professional global proxy IP provider. Its highlights include a pay-as-you-go recharge model, comprehensive proxy types, and a simple and efficient user interface.Proxy302
是一个专业的全球代理IP采购平台,即充即用的充值方式、最全面的代理类型以及简洁高效的用户界面是Proxy302的亮点。Proxy302 uses a token-based recharge system, allowing for instant use upon recharge. Tokens (PTC) are equivalent to U.S. dollars, and the recharge amount can be used to generate all types of proxy IPs without the need for bundled monthly subscription packages.
Proxy302采用充值代币的方式,即充即用。代币(PTC)等值$美元,充值额度适用于生成所有类型的代理IP,无需进行月付套餐捆绑购买。
Proxy302's proxy types include 'Dynamic IP charged by traffic,' 'Dynamic IP charged by IP,' 'Static IP charged by traffic,' and 'Static IP charged by IP.' Static proxy IPs are further categorized into residential IPs and data center IPs, which can meet various business needs.
Proxy302的代理类型分为【动态IP按流量扣费】、【动态IP按IP扣费】、【静态IP按流量扣费】、【静态IP按IP扣费】,静态代理IP还分为住宅IP、数据中心IP,能满足各类业务需求。
Proxy302's user interface is user-friendly with full-funtions. It offers a free browser extention for one-click proxy setup. Users can generate IPs, set up proxies, recharge, view traffic statistics, check balances all in one stop.
Proxy302用户界面简洁而不简单,易用且高效;提供免费浏览器插件,实现一键设置代理;用户通过用户界面实现生成IP、设置代理、充值、流量统计、检查余额等功能。
Proxy302 offers new users a free trial credit equivalent to $1, which can be used to test all types of proxy IPs. Additionally, there is a special $5 discount trial package for newcomers!
Proxy302为新用户提供等额$1的免费测试额度,该测试额度适用于测试所有类型的代理IP,且设有新人$5优惠体验套餐!
How to setup?
如何设置?
1. Log in to Proxy302 and generate a proxy
1. 登录Proxy302并获取代理
- Example as [Static IP-Charge by Traffic]
- 以静态代理为例,点击Static IP >Charge by Traffic
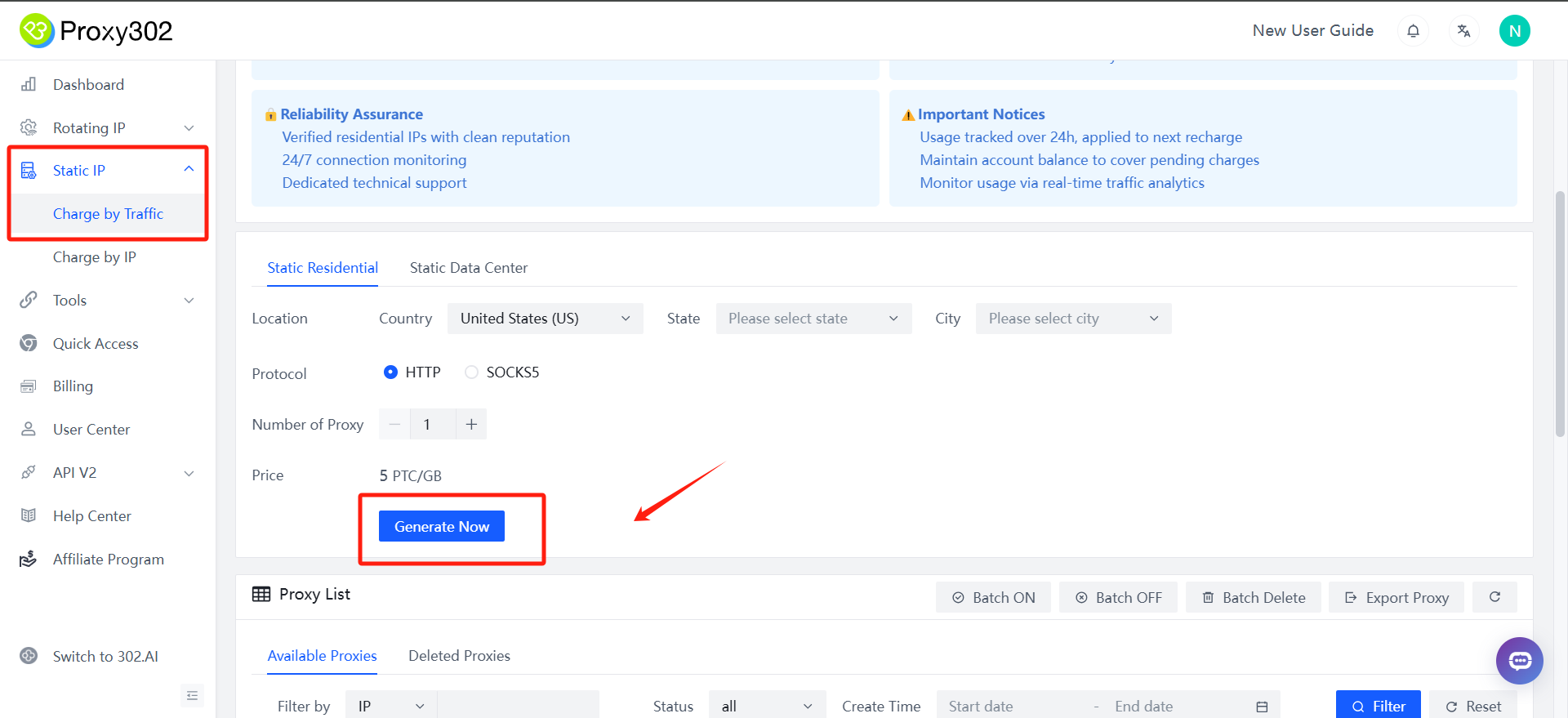
2. Copy Proxy302 proxy information [HOST: PORT: USER: PASS]
2. 拷贝Proxy302的代理信息[HOST: PORT: USER: PASS]
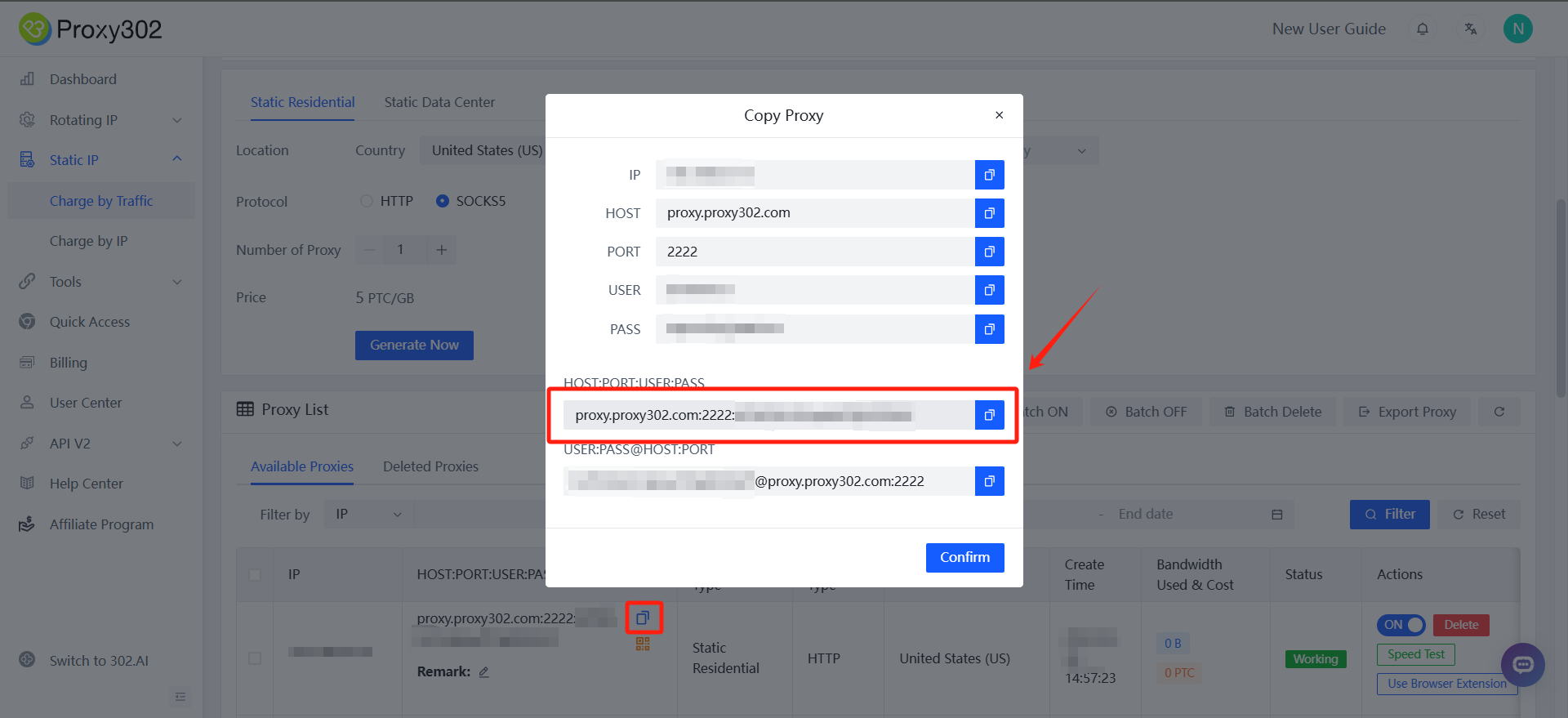
3. Log in to ixBrowser, click Browser Profile, select Profile List, click Create Profile
3. 登录ixBrowser,点击浏览器窗口 > 窗口列表,点击创建窗口
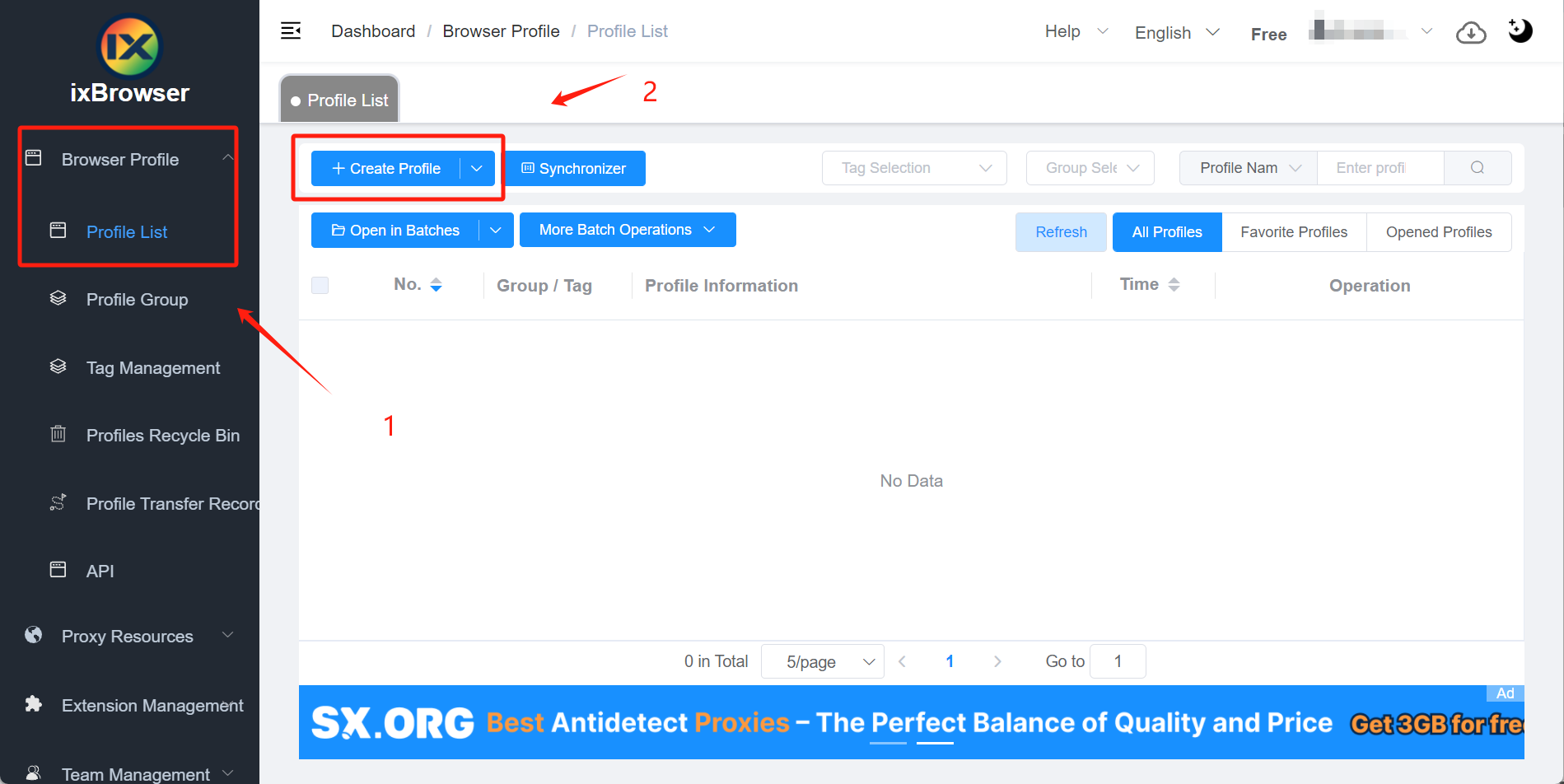
4. Fill in the proxy configuration in the box, click the "Proxy Host" input box, paste the proxy [HOST: PORT: USER: PASS]
4. 在代理配置界面填写入从Proxy302获取的代理信息[HOST: PORT: USER: PASS]
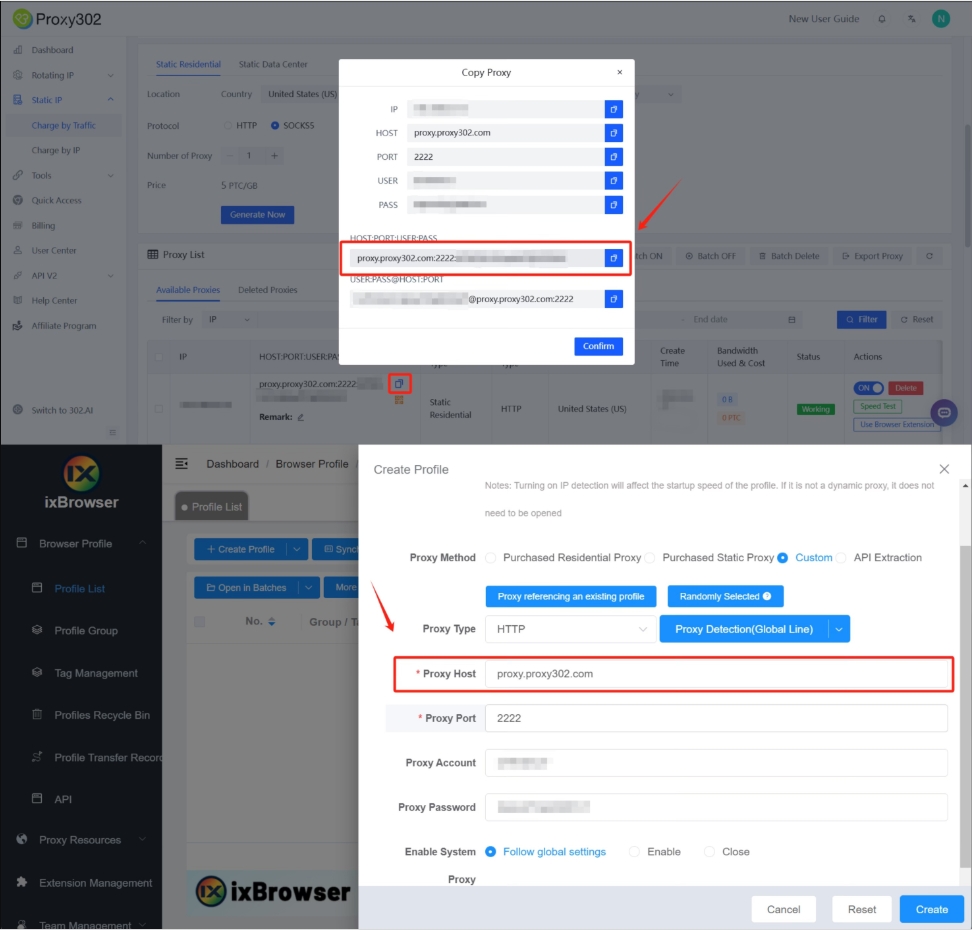
5. Click the "Proxy Detection" button to check whether the proxy connection is successful
5. 点击代理检测按钮来确认代理连通性
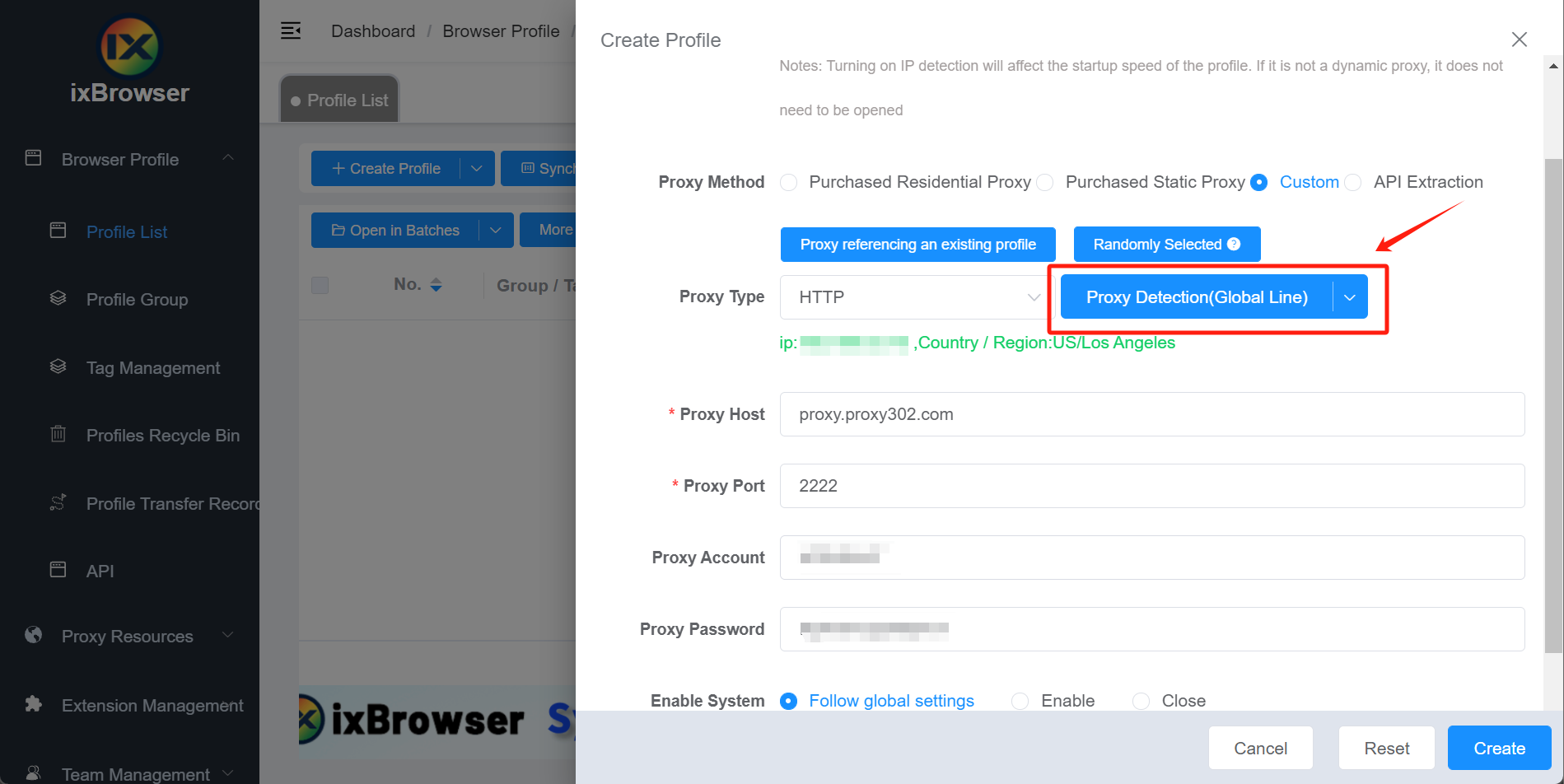
6. Click the "Create" button to set up the proxy successfully
6. 点击立即创建按钮完成代理设置及窗口创建操作
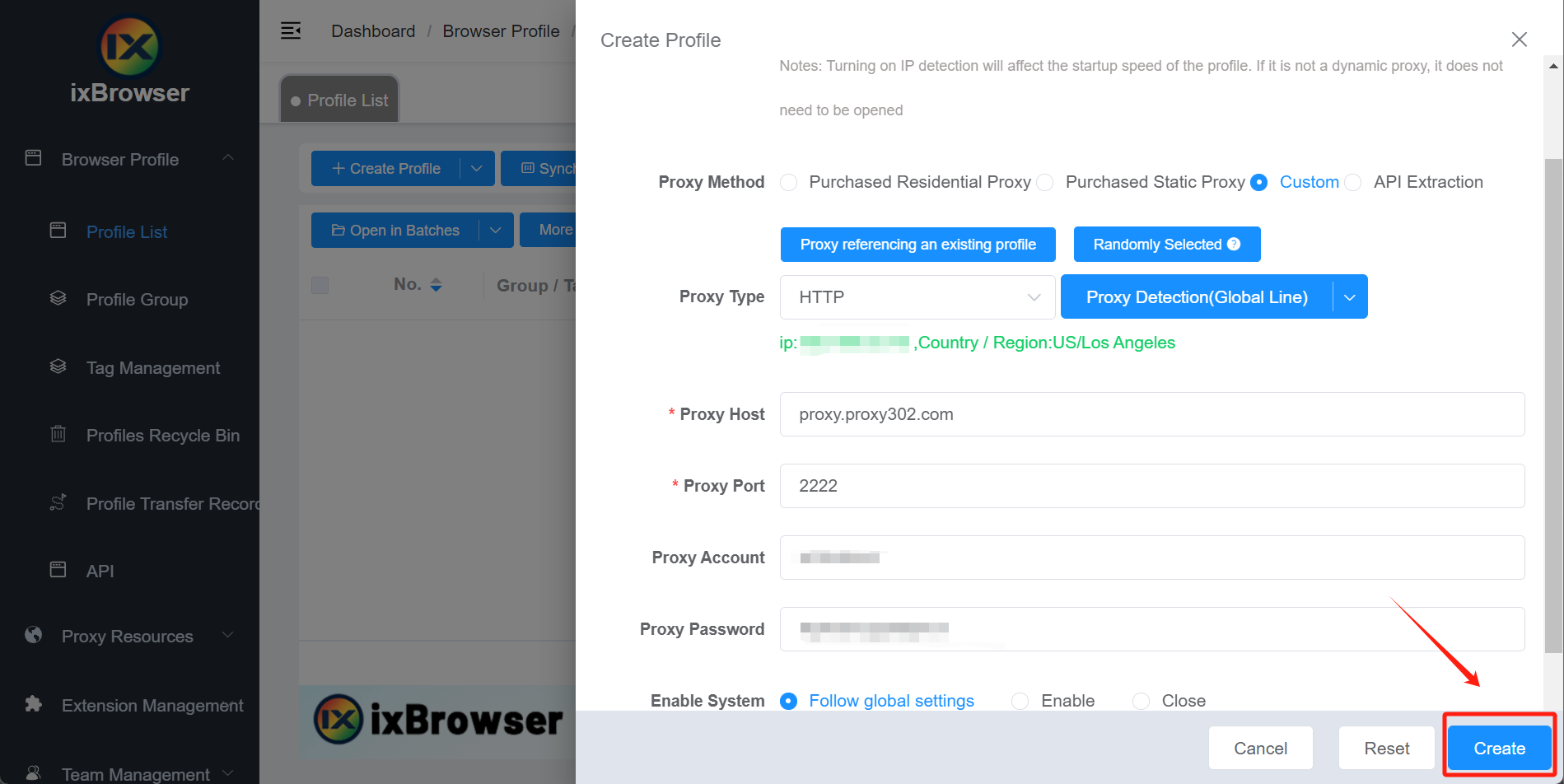
7. Click the "Open" button of the corresponding serial number
7. 点击窗口右侧的打开按钮
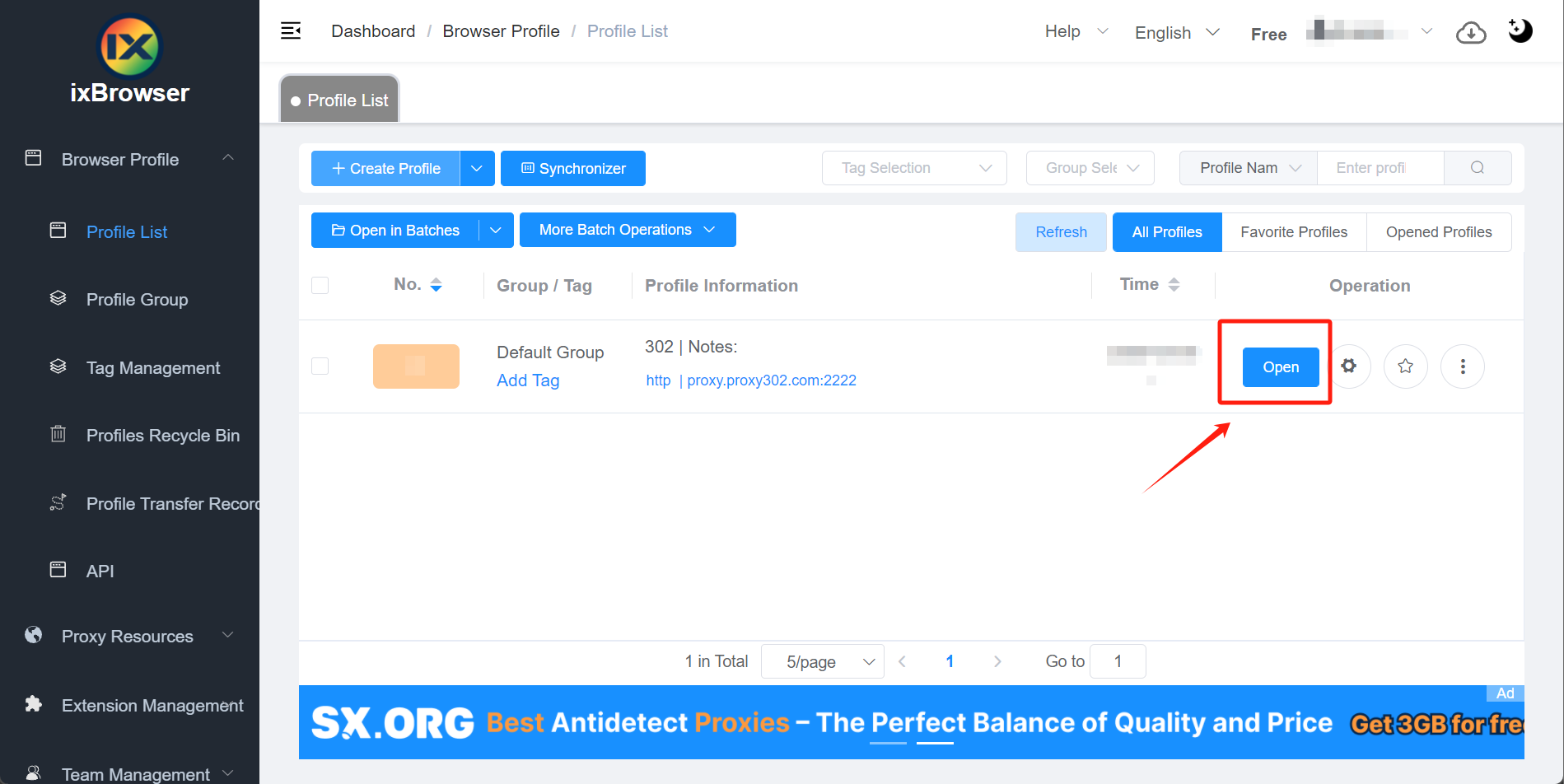
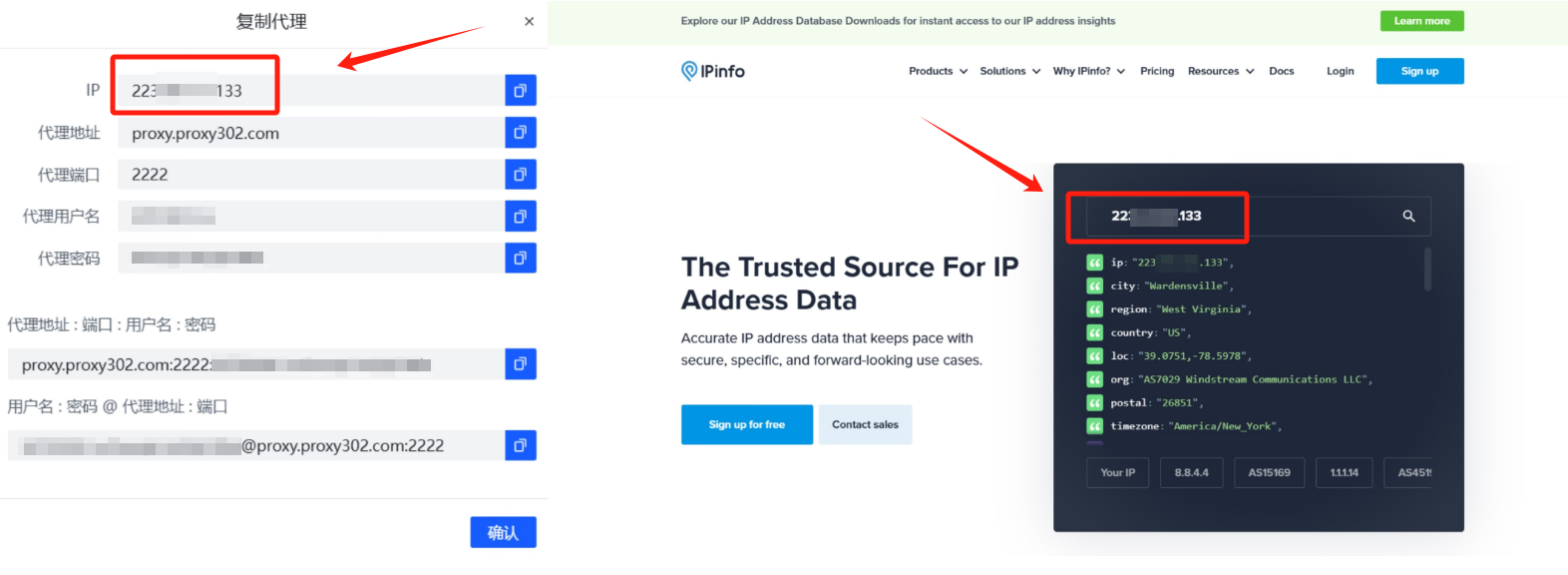
8. Enter "ipinfo.io" in the web page. If the IP address on the page is the same as the proxy IP address, the proxy IP address is set successfully
8. 在窗口内输入ipinfo.io, 如果检测出的IP地址与你所填入的IP地址相同,则说明配置成功